Error: Some users added as members to a Microsoft 365 group in Outlook on the web may be given “Owner” permissions by default
Important Security Notice for M365 Groups
Between October 3 and October 31, 2025, Microsoft Exchange Online experienced an issue that affected Microsoft 365 (M365) Groups. During this period, when a new user was added to a group—either by a team member or by IT via the web interface (OWA/Outlook on the web)—the user was incorrectly assigned Owner (group admin) permissions instead of a standard Member. This issue persisted for nearly a month.
If a user was unintentionally granted Owner permissions, they could potentially:
-
Delete all content within the group
-
Add additional users, including external users from other organizations
Because modern workplaces often allow users to manage their own groups, this flaw posed a higher security risk.
We recommend that all M365 administrators review the owners of their groups and ensure that only authorized users have admin rights. If you find unexpected owners, it is important to check when they were added and verify whether it occurred during October 2025.
Export All Groups to CSV
Below is a modified PowerShell script that will connect to your tenant and export all groups to a CSV file. This allows you to audit group owners and membership quickly.
This version:
-
Highlights Owner and Member consistently.
-
Asks for a path to store the export file
# Read Group Owner membership to check if you are affected by EX1181125, Some users added as members to a Microsoft 365 group in Outlook on the web may be given "Owner" permissions by default
# V1.0, 05.11.2025, www.butsch.ch
# Connect to Exchange Online
Connect-ExchangeOnline -ShowBanner:$False
# Ask user for export path with default
$DefaultPath = "C:\Temp"
$ExportFolder = Read-Host "Enter export folder path (default: $DefaultPath)"
if ([string]::IsNullOrWhiteSpace($ExportFolder)) {
$ExportFolder = $DefaultPath
}
# Create folder if it does not exist
if (-not (Test-Path -Path $ExportFolder)) {
try {
New-Item -Path $ExportFolder -ItemType Directory -Force | Out-Null
Write-Host "Folder created: $ExportFolder"
} catch {
Write-Error "Failed to create folder: $_"
exit
}
}
# Build export file name with current date
$DateString = (Get-Date).ToString("dd_MM_yyyy")
$ExportFile = Join-Path -Path $ExportFolder -ChildPath "${DateString}_M365_Group_Owner.txt"
# Get all Office 365 Groups
$GroupData = @()
try {
$Groups = Get-UnifiedGroup -ResultSize Unlimited -SortBy Name
} catch {
Write-Error "Failed to retrieve groups: $_"
Disconnect-ExchangeOnline -Confirm:$False
exit
}
# Loop through each Group
foreach ($Group in $Groups) {
try {
$GroupOwners = Get-UnifiedGroupLinks -LinkType Owners -Identity $Group.Id |
Select-Object DisplayName, PrimarySmtpAddress
$GroupData += [PSCustomObject]@{
GroupName = $Group.Alias
GroupEmail = $Group.PrimarySmtpAddress
OwnerName = ($GroupOwners.DisplayName -join "; ")
OwnerIDs = ($GroupOwners.PrimarySmtpAddress -join "; ")
}
} catch {
Write-Warning "Failed to retrieve owners for group $($Group.Alias): $_"
}
}
# Export to tab-delimited TXT
try {
$GroupData | Export-Csv -Path $ExportFile -Delimiter "`t" -NoTypeInformation -Force
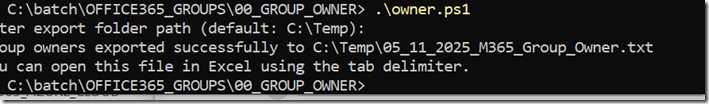
Write-Host "Group owners exported successfully to $ExportFile"
Write-Host "You can open this file in Excel using the tab delimiter."
} catch {
Write-Error "Failed to export TXT: $_"
}
# Disconnect Exchange Online
Disconnect-ExchangeOnline -Confirm:$False
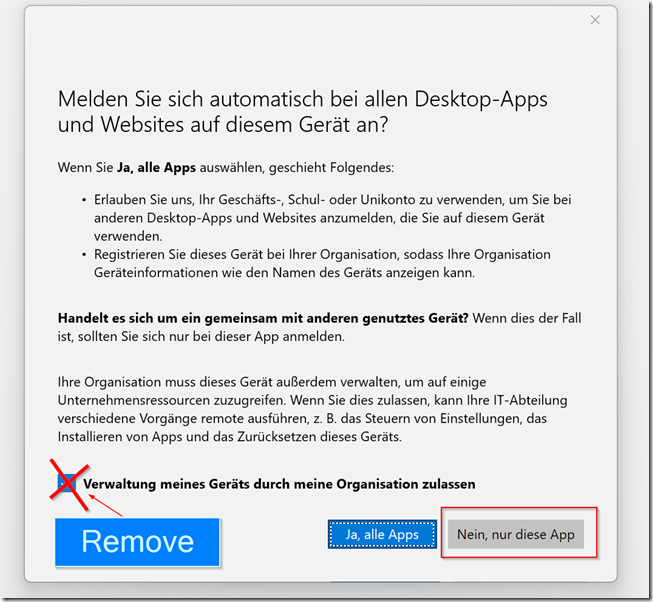
If you connect to a customer that manages devices with Intune make sure YOU deselect the BOX right and choose “NO, only this app”. You just need READ access for the report and don’t want the Tenant to manage your IT device.
Original Issue Text:
User impact: Users added as members to a Microsoft 365 group in Outlook on the web may be given “Owner” permissions by default.
More info: Specifically, this issue occurred when users were added as members to the group through Outlook on the web.
Final status: We’ve confirmed using internal testing that our code fix remediated the impact.
Scope of impact: Some users added as members to a Microsoft 365 group in Outlook on the web may have been given “Owner” permissions by default instead of “Member” permissions.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.