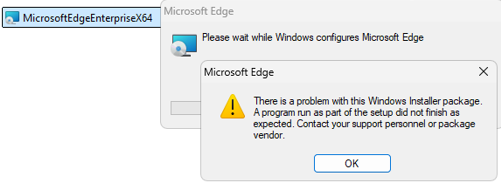
Microsoft EDGE fails to Update from WSUS, from MSI-file or repair APPS because of GPO, 0x80070643, 1722
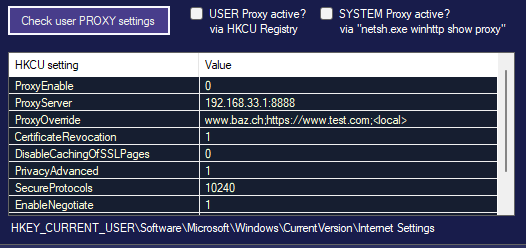
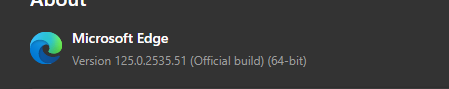
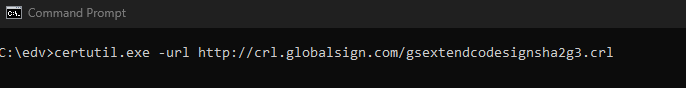
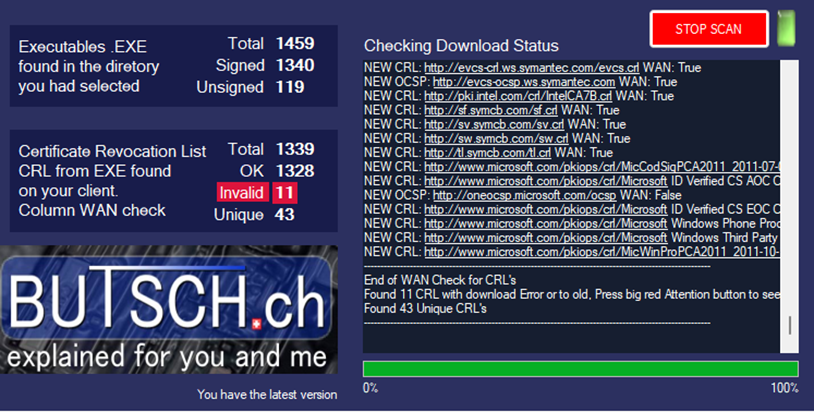
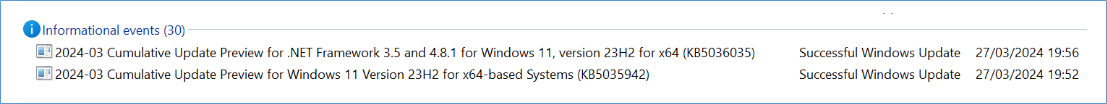
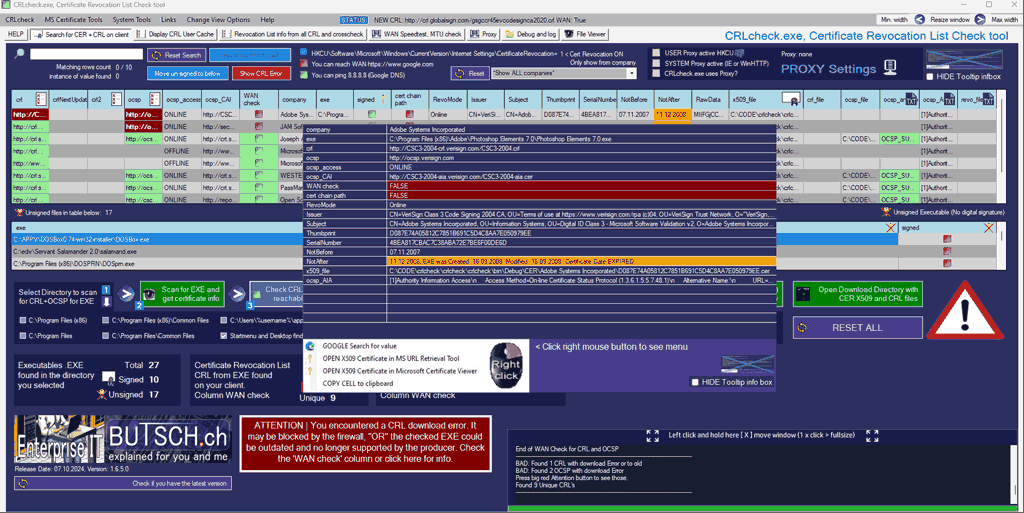
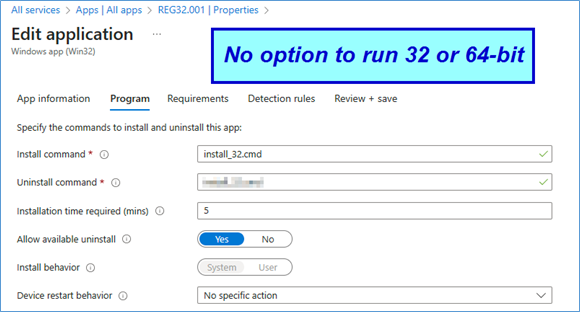
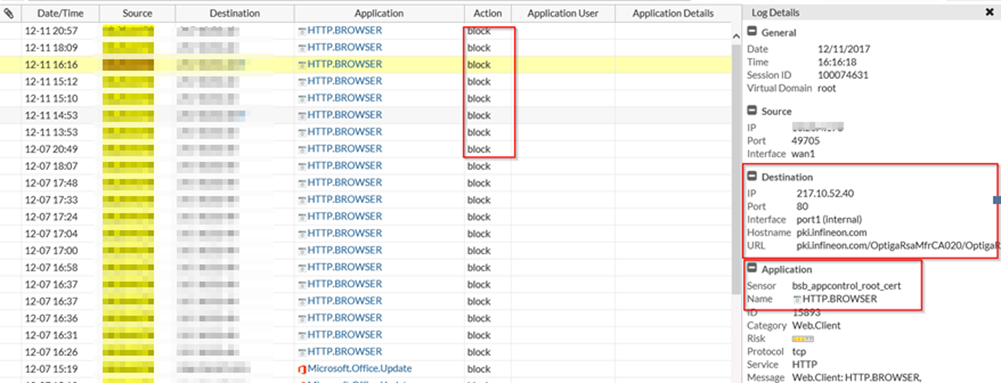
Microsoft EDGE fails to Update from WSUS, from MSI-file or repair APPS because of GPO, 0x80070643, 1722 Cause: GPO / EdgeUpdate Policies In this case, we have a GPO (Group Policy) created by or for a customer who uses Firefox as the default browser because a Citrix engineer advised them that this was the best […]