Trellix ePolicy Orchestrator 5.10.0 Service Pack 1 Update 4
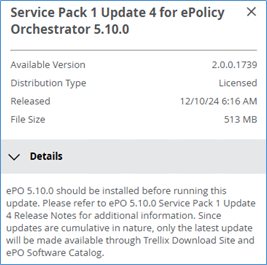
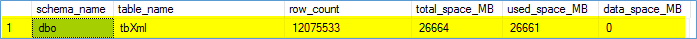
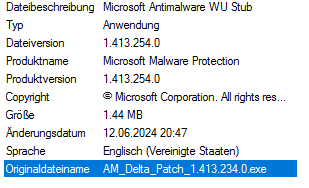
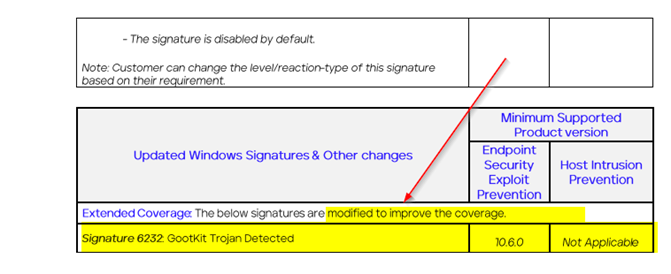
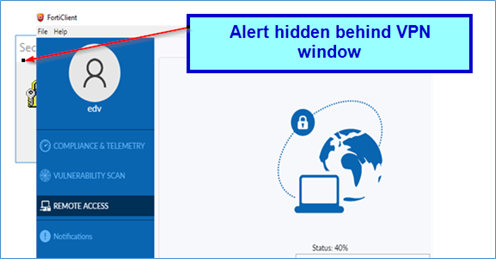
Trellix ePolicy Orchestrator 5.10.0 Service Pack 1 Update 4 We have installed the latest Update 4 on several customer on-premises EPO installation and the update works fine and without any problems. Key Considerations for Updating Trellix ePO 5.10 SP1 to the Latest Rollup 4 Check your ePO database size. Some Trellix SP or Rollup […]