- Download IE10 for Windows 7, http://windows.microsoft.com/en-us/internet-explorer/downloads/ie-10/worldwide-languages
-
Block IE10 on all system which are NOT connected to Windows Update Server WSUS, http://www.microsoft.com/en-us/download/details.aspx?id=36512
Notes in German from the field:
- Kommt nicht automatisch WENN WSUS Anbindung vorhanden
- Kommt automatisch bei allen kleinen Kunden die KEIN WSUS haben da gestuft als “important Update”
Toolkit to Disable Automatic Delivery of Internet Explorer 10
http://www.microsoft.com/en-us/download/details.aspx?id=36512
- For computers running Windows 7 or Windows Server 2008 R2, the Blocker Toolkit prevents the machine from receiving Internet Explorer 10 via Automatic Updates on the Windows Update and Microsoft Update sites.
- The Blocker Toolkit will not prevent users from manually installing Internet Explorer 10 from the Microsoft Download Center, or from external media.
- Organizations do not need to deploy the Blocker Toolkit in environments managed with an update management solution such as Windows Server Update Services or Systems Management Server 2003. Organizations can use those products to fully manage deployment of updates released through Windows Update and Microsoft Update, including Internet Explorer 10, within their environment.
- Even if you used the Blocker Toolkit to block Internet Explorer 8 or Internet Explorer 9 from being installed as a high-priority or important update, you will still need to use the Internet Explorer 10 version of the Blocker Toolkit to block Internet Explorer 10 from being installed. There are different registry keys used to block or unblock automatic delivery of Internet Explorer 8, Internet Explorer 9 and Internet Explorer 10.
Files within the EXE
HKLM\SOFTWARE\Microsoft\Internet Explorer\Setup\10.0\
DoNotAllowIE10 =1
Toolkit to Disable Automatic Delivery of Internet Explorer 10
Overview
To help our customers become more secure and up-to-date, Microsoft will distribute Internet Explorer 10 as a high-priority update through Automatic Updates for Windows 7 Service Pack 1 (SP1) x86 and x64, and Windows Server 2008 R2 SP1 x64. This Blocker Toolkit is intended for organizations that would like to block automatic delivery of Internet Explorer 10 to machines in environments where Automatic Updates is enabled. The Blocker Toolkit will not expire.
- For computers running Windows 7 or Windows Server 2008 R2, the Blocker Toolkit prevents the machine from receiving Internet Explorer 10 via Automatic Updates on the Windows Update and Microsoft Update sites.
- The Blocker Toolkit will not prevent users from manually installing Internet Explorer 10 from the Microsoft Download Center, or from external media.
- Organizations do not need to deploy the Blocker Toolkit in environments managed with an update management solution such as Windows Server Update Services or Systems Management Server 2003. Organizations can use those products to fully manage deployment of updates released through Windows Update and Microsoft Update, including Internet Explorer 10, within their environment.
- If you used the Blocker Toolkit to block Internet Explorer 9 from being installed as a high-priority update, you need to use the Internet Explorer 10 version of the Blocker Toolkit to block Internet Explorer 10 from being installed. There are different registry keys used to block or unblock automatic delivery of Internet Explorer 9 and Internet Explorer 10.
Toolkit Components
This toolkit contains two components:
- An executable blocker script
- A Group Policy Administrative Template (.ADM file)
Supported Operating Systems
Windows 7 Service Pack 1 (SP1) x86 and x64 and Windows Server 2008 R2 SP1 x64
Blocker Script
The script creates a registry key and sets the associated value to block or unblock (depending on the command-line option used) automatic delivery of Internet Explorer 10 on either the local machine or a remote target machine.
Registry key: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Setup\10.0
Key value name: DoNotAllowIE10
|
Value |
Result |
|
Key is not defined |
Distribution is not blocked. |
|
0 |
Distribution is not blocked. |
|
1 |
Distribution is blocked. |
The script has the following command-line syntax:
IE10_Blocker.cmd [<machine name>] [/B] [/U] [/H]
Machine Name
The <machine name> parameter is optional. If not specified, the action is performed on the local machine. Otherwise, the remote machine is accessed through the remote registry capabilities of the REG command. If the remote registry can’t be accessed due to security permissions or the remote machine can’t be found, an error message is returned from the REG command.
Switches
Switches used by the script are mutually exclusive and only the first valid switch from a given command is acted on. The script can be run multiple times on the same machine.
|
Switch |
Description |
|
/B |
Blocks distribution |
|
/U |
Unblocks distribution |
|
/H (or /?) |
Displays the following summary help: This tool can be used to remotely block or unblock the delivery of Internet Explorer 10 through Automatic Updates.
———————————————————— Usage: IE10_Blocker.cmd [<machine name>] [/B][/U][/H] B = Block Internet Explorer 10 deployment U = Allow Internet Explorer 10 deployment H = Help Examples: IE10_Blocker.cmd mymachine /B (blocks delivery on machine “mymachine”)
IE10_Blocker.cmd /U (unblocks delivery on the local machine) ———————————————————— |
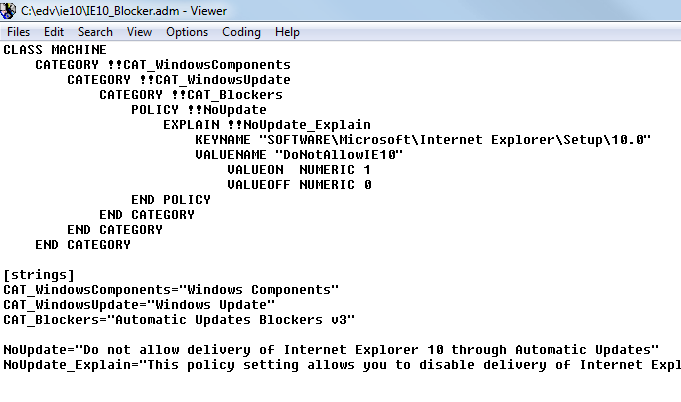
Group Policy Administrative Template (.ADM file)
The Group Policy Administrative Template (.ADM file) allows administrators to import the new Group Policy settings to block or unblock automatic delivery of Internet Explorer 10 into their Group Policy environment, and use Group Policy to centrally execute the action across systems in their environment.
Users running Windows 7 (SP1) or Windows Server 2008 R2 (SP1) will see the policy under Computer Configuration / Administrative Templates / Classic Administrative Templates / Windows Components / Windows Update / Automatic Updates Blockers v3. This setting is available only as a Computer setting; there is no Per-User setting.
Note: This registry setting is not stored in a policies key and is thus considered a preference. Therefore if the Group Policy Object that implements the setting is ever removed or the policy is set to Not Configured, the setting will remain. To unblock distribution of Internet Explorer 10 by using Group Policy, set the policy to Disabled.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.