Unable to Install VSE 8.8 Patch 2 and 3 to Windows XP SP3 clients after 31.12.2013
Error: ERROR: ParseXMLFile: signature check failed
Products: Windows XP SP3 and Mcafee VSE 8.8 Patch 2 and Patch 3
Workaround: Integrate VSE 8.8 RTM (First Release) in EPO TREE (Test) and deploy
Final: Wait for VSE 8.8 Patch 4
Error in File on client:
\\client\c$\WINDOWS\Temp\McAfeeLogs\vse8.8.0.core*.*
There has been complex and even strange solutions provide by Microsoft for that problem. Set back date, take out machine from Domain, Export and delete Certificates etc. This is clear not a Mcafee issue and is related to signing and trusting Executables and some root Cert which is included in Window XP SP3. This certificate should expire MAY 2014 and not 31.12.2013 (End of support Windows XP)
https://kc.mcafee.com/corporate/index?page=content&id=KB77683
The issues should be resolved with Patch 4 for VSE 8.8 which will be released in FEB 2014.
In the meantime the only solutions which seams valid of you have a small amount with the problem is to ROLL OUT VSE 8.8 RTM and then waits until Patch 4.
Major problem is that you can’t download the files from actual Website even with a valid NAI licence number. Its’ unclear why Mcafee does not allow that.
Also you can’t check in into the “actual” Software Archive because you already have the version VSE 8.8 P3 there. A workaround is to include (Check in) the older version in the “Before” or “Test” Archives in your EPO.
Then from there DEPLOY that older version to the mentioned clients in a separate task in EPO. When VSE 8.8 Patch 4 comes this should be solved.
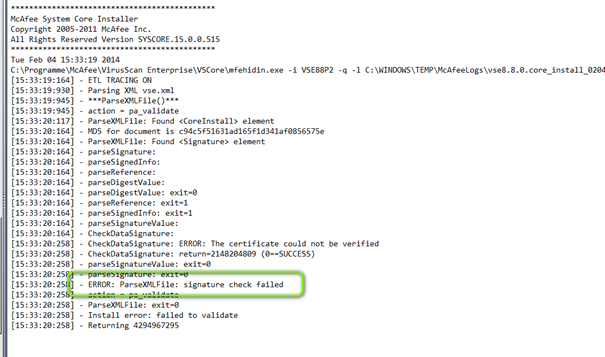
[09:35:11:378] – ETL TRACING ON
[09:35:11:550] – Parsing XML vse.xml
[09:35:11:550] – ***ParseXMLFile()***
[09:35:11:550] – action = pa_validate
[09:35:11:691] – ParseXMLFile: Found <CoreInstall> element
[09:35:11:691] – MD5 for document is c94c5f51631ad165f1d341af0856575e
[09:35:11:691] – ParseXMLFile: Found <Signature> element
[09:35:11:691] – parseSignature:
[09:35:11:691] – parseSignedInfo:
[09:35:11:691] – parseReference:
[09:35:11:691] – parseDigestValue:
[09:35:11:691] – parseDigestValue: exit=0
[09:35:11:691] – parseReference: exit=1
[09:35:11:691] – parseSignedInfo: exit=1
[09:35:11:691] – parseSignatureValue:
[09:35:11:691] – CheckDataSignature:
[09:35:11:831] – CheckDataSignature: ERROR: The certificate could not be verified
[09:35:11:831] – CheckDataSignature: return=2148204809 (0==SUCCESS)
[09:35:11:831] – parseSignatureValue: exit=0
[09:35:11:831] – parseSignature: exit=0
[09:35:11:831] – ERROR: ParseXMLFile: signature check failed
[09:35:11:831] – action = pa_validate
[09:35:11:831] – ParseXMLFile: exit=0
[09:35:11:831] – Install error: failed to validate
[09:35:11:831] – Returning 4294967295


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.