Microsoft Office Security Feature Bypass Vulnerability
CVE-2026-21509, Security Vulnerability, Released: Jan 26, 2026, Last updated: Jan 26, 2026
- Assigning CNA
- Microsoft
- CVE.org link
- CVE-2026-21509
- Impact
- Security Feature Bypass
- Max Severity
- Important
- CVSS Source
- Microsoft
- Vector String
CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:F/RL:O/RC:C
- Metrics
- CVSS:3.1 7.8 / 7.2
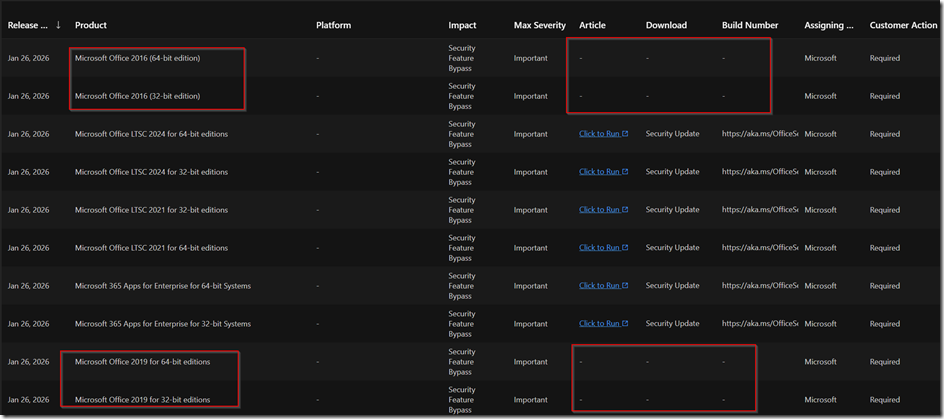
Problem 22:19 o’clock there is no Office 2016 or 2019 out-of-band-patch
Status 26.01.2026 MS brings only patches for enterprise LTSC first and others have to wait
@echo off
setlocal EnableExtensions
:: ========================================================================================================
:: V1.0, 26.01.2026, www.butsch.ch, First release because no Out-of-band-for-OF2016_OF2019
:: ========================================================================================================
:: CVE-2026-21509 Office COM Compatibility Registry Mitigation
:: Enterprise-ready: 32/64-bit OS, 32/64-bit Office
:: Includes elevated check
:: Use at own risk
:: READ: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2026-21509
:: Needs to run elevated from cmd.exe
:: ========================================================================================================
:: Test our freeware CRLcheck.exe to automate security check of Code sign certificates and CRL + OCSP
:: ========================================================================================================
:: <a href="https://www.butsch.ch/post/crlcheck-exe-certificate-revocation-list-check-tool-to-verify-all-crl-and-ocsp-on-windows-client/">CRLcheck.exe Certificate Revocation List Check Tool to verify all CRL and OCSP on Windows client - www.butsch.ch
:: --- Elevation check
net session >nul 2>&1
if errorlevel 1 (
echo ERROR: Run this script as Administrator
exit /b 1
)
:: --- CLSID and DWORD
set CLSID={EAB22AC3-30C1-11CF-A7EB-0000C05BAE0B}
set FLAG_DEC=1024
set FLAG_HEX=0x00000400
:: --- Detect Outlook.exe path safely
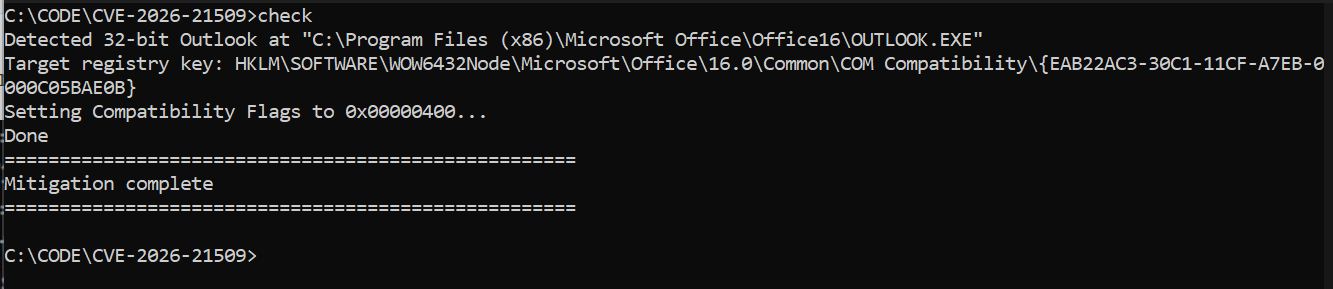
set "OUTLOOK32=C:\Program Files (x86)\Microsoft Office\Office16\OUTLOOK.EXE"
set "OUTLOOK64=C:\Program Files\Microsoft Office\Office16\OUTLOOK.EXE"
if exist "%OUTLOOK32%" (
set "BASEKEY=HKLM\SOFTWARE\WOW6432Node\Microsoft\Office\16.0\Common\COM Compatibility"
echo Detected 32-bit Outlook at "%OUTLOOK32%"
) else if exist "%OUTLOOK64%" (
set "BASEKEY=HKLM\SOFTWARE\Microsoft\Office\16.0\Common\COM Compatibility"
echo Detected 64-bit Outlook at "%OUTLOOK64%"
) else (
echo ERROR: Outlook.exe not found
exit /b 2
)
echo Target registry key: %BASEKEY%\%CLSID%
:: --- Ensure COM Compatibility base key exists
reg query "%BASEKEY%" >nul 2>&1 || (
echo Creating COM Compatibility key...
reg add "%BASEKEY%" /f >nul
)
:: --- Ensure CLSID key exists
reg query "%BASEKEY%\%CLSID%" >nul 2>&1 || (
echo Creating CLSID key...
reg add "%BASEKEY%\%CLSID%" /f >nul
)
:: --- Set Compatibility Flags
for /f "tokens=3" %%A in (
'reg query "%BASEKEY%\%CLSID%" /v "Compatibility Flags" 2^>nul ^| find "Compatibility Flags"'
) do set CURRENT_FLAG=%%A
if "%CURRENT_FLAG%"=="%FLAG_HEX%" (
echo Compatibility Flags already correct
) else (
echo Setting Compatibility Flags to %FLAG_HEX%...
reg add "%BASEKEY%\%CLSID%" /v "Compatibility Flags" /t REG_DWORD /d %FLAG_DEC% /f >nul
echo Done
)
echo ====================================================
echo Mitigation complete
echo ====================================================
exit /b 0
CVE + MS LINK:
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2026-21509
https://www.cve.org/CVERecord?id=CVE-2026-21509


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.