Introduction:
Event logs provide valuable insights into system operations, allowing IT professionals to monitor and troubleshoot potential issues. When dealing with Windows event logs, PowerShell is a powerful tool that enables event filtering, but it may not be everyone’s preferred choice due to complexity and perceived security concerns. In this blog post, we will explore an alternative method – using the command-line filter of Event Viewer – to easily access Critical, Error, and Warning events from the Application log.
|
In this command, we construct an XML query that filters events based on severity levels: Level=1 corresponds to Critical, Level=2 corresponds to Error, and Level=3 corresponds to Warning. The command will open the Event Viewer and present the filtered results, saving valuable time for IT operations and support personnel. |
|
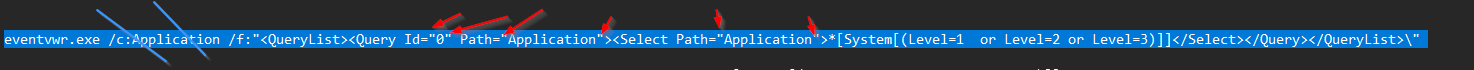
eventvwr.exe /f:”<QueryList><Query Id=’0′ Path=’Application’><Select Path=’Application’>*[System[(Level=1 or Level=2 or Level=3)]]</Select></Query></QueryList>\” |
Advantages of the Command-Line Filter:
Familiarity: Many seasoned IT professionals prefer using a simple command-line approach they are familiar with, making it easier to find and work with event logs efficiently.
Accessibility: The command-line filter is available on all modern Windows operating systems, eliminating compatibility concerns.
Trustworthy: Since the command-line tool is a built-in Windows feature, there are no worries about third-party dependencies or security issues.
PowerShell Approach:
Before diving into the command-line filter, let’s quickly review the PowerShell method. By leveraging the Get-EventLog cmdlet, one can filter events based on severity levels and display them in PowerShell console. The script would look like this:
Get-EventLog -LogName “Application” -EntryType Error, Warning, Information | Where-Object { $_.EntryType -eq “Error” -or $_.EntryType -eq “Warning” -or $_.EntryType -eq “Information” }
But we want it commandline style because most people with long term expierence are used to that tool/console to find and work.
eventvwr.exe /h

What? 😉
Ok let’s try:
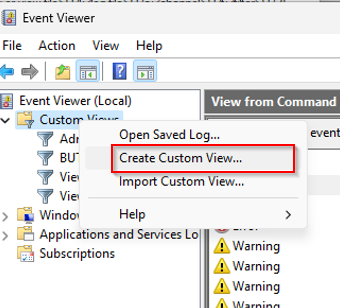
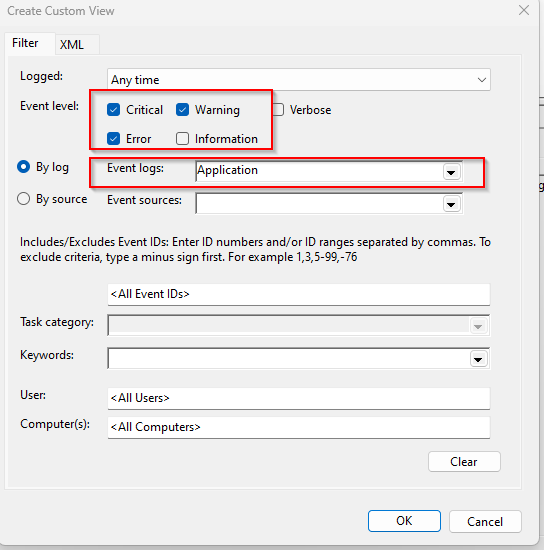
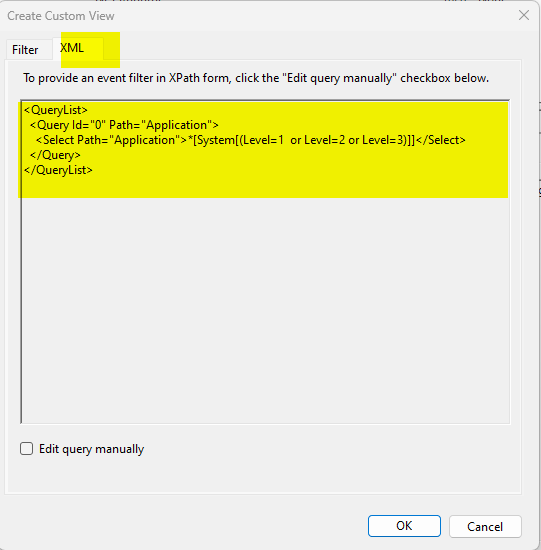
Go to XML tab
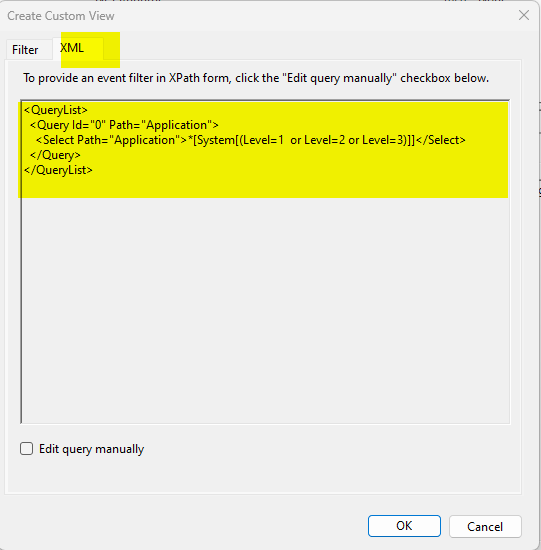
Cut and paste into notepad
<QueryList>
<Query Id=”0″ Path=”Application”>
<Select Path=”Application”>*[System[(Level=1 or Level=2 or Level=3)]]</Select>
</Query>
</QueryList>
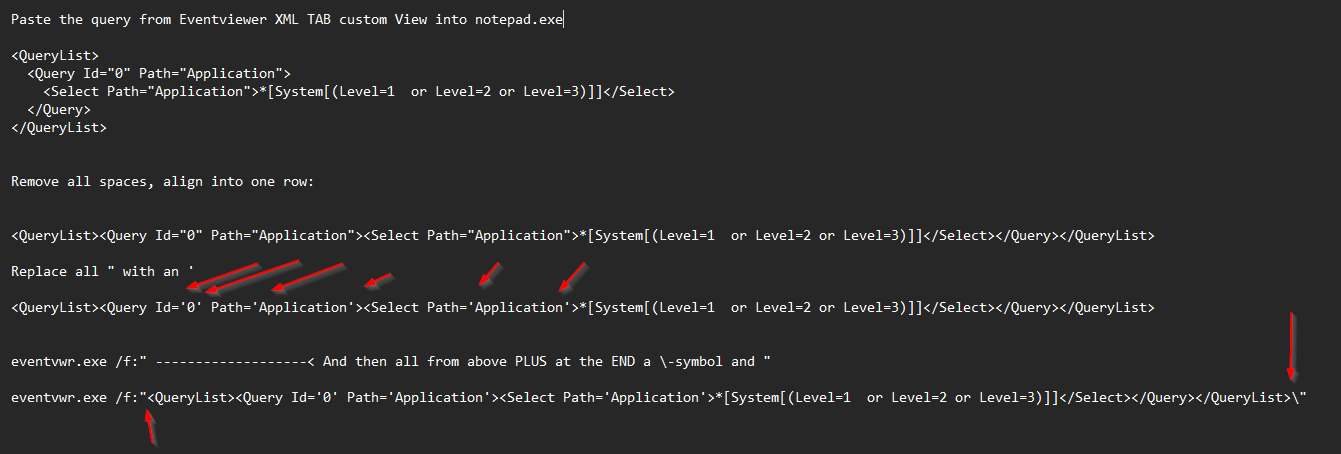
If you see this than all fine:
If you see this than you did not read 100% and checked all ” > ‘ and the \ at the end or you try to
call together with /c:application (Channel) and Query (/f:)
Wrong sample:
Some Microsoft Links (One sample is wrong there and I did not understand what he tells at once and the eventvwr.exe /h is really nerdy? 😉


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.