Problem:
You have to renew an Exchanger SAN/UC-Certificate and you can’t do this anymore after 2015 because it contains a NON EXTERNAL First Level Extension like “.LOCAL”.
- Rename the Full Windows Domain in a 1 year project and have fun
- Integrate a SPLIT DNS as below, Bend all Exchange URL to the same FQDN
Main Technet Link:
http://support.microsoft.com/kb/940726/en-us
I personally don’t like this solution since you may in most complex case end up in trouble with some special cases like “RPC-over-HTTP” (Outlook anywhere) and some Autodiscover functions.
On the other side don’t like Wildcard Certs for this because if you have that the other departments want to use the same Certificate and at the end everyone uses it. Worst it lays around on laptops and Servers then if you don’t Controll it strict.
Currently still March 2015 this is the only solution quick and fast if you customer has a First Level Windows Domain with .LOCAL. Most it’s urgent because Cert has expired.
Just to mention that there is another way but this needs planning and time
Enterprise way:
Internal Domain: Cover these with your own internal Certificate Authority (Ask if you have one, make a project separate for that because it’s sensitive and complex) .
External Domain: Use a Cert Provider SAN/UC-Certificate as we had before for all external FQDN
This enterprise mix however leads us to splitting the CAS/OWA Directories on separates SITES within the IIS (Because of only 1 Cert per IIS-Site) or we make single separate CAS Server for internal and external (Which Microsoft does not want us).
On the other side if we have Load Balancers for the CAS mostly those separate CAS are not in the Load Balancer HA team.
Timeline for SAN/UC Certs with Local ending or non-external First level (www.technet.local)
https://www.butsch.ch/post/Exchange-Certificates-Aenderung-CAS-Outlook-mit-local-Domain.aspx

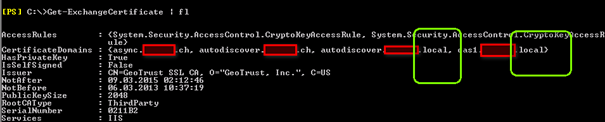
Such a SAN Certificate which includes LOCAL is not valid anymore after some date. And you can’t reorder it. (Screenshot)
Powershell: Get-exchangecertificate | fl
In Green BOX there are the First Level Domains .LOCAL Domains that you can’t COVERY anymore in ONE Cert in 2015.
INTERNAL DNS NAME: customer.local (The Active Directory Domain)
EXTERNAL DNS NAME: customer.ch (Your Webserver, FTP, MX-E-Mail Domain from external)
Third level DOMAIN: async.customer.ch
Why can’t I renew?
Because we can’t make a UC/SAN-certificate after November 2015 anymore we have to convert the DNS into SPLIT DNS setup. That means we copy the Extern DNS into Internal DNS. Even if you CAN renew it WILL only run until November 2015 with some Cert Issuer.
https://www.butsch.ch/post/Exchange-Certificates-Aenderung-CAS-Outlook-mit-local-Domain.aspx
Make the SPLIT DNS
See links at end for more help on the SPLIT DNS.
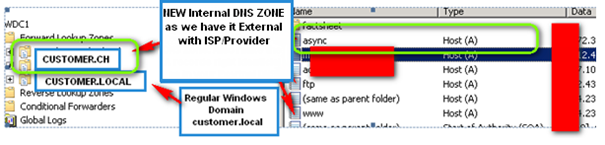
SPLIT DNS Copy External ZONE File to internal Active Directory DNS
- Get the info from External ZONE file from the Provider ISP like customer.ch. Ask them you need an extract (copy) of the ZONE file for your external Domain.
- Do a new Active Directory integrated Forward ZONE File with same name “customer.ch” internal
- Make the A-Records internal so INTERNAL users can reach www and ftp also from internal (These are shown on the right side). Make “FTP”, “WWW” point to same IP as the external. (If you don’t do that your INTERNAL users will not be able to reach the External Website or Cloud Service you use with your ISP)
- The ASYNC in OUR sample POINTS to the IP of the Exchange 2010 CAS
- On the External DNS the ASYNC points to our Firewall and then to the Exchange 2010 CAS
This is how this may look.
Get the NEW SINGLE FQDN Certificate
- Next if you are sure this works Generate the Certificate Request (https://www.butsch.ch/post/Generate-SAN-UC-Certificate-SSL-on-Exchange-2010.aspx)
- Keep in MIND you need NO SAN/UC just one SINGLE Certificate with ONE FQDN for all
- Send Request to provider
- Integrate the Certificate you get in Exchange (But Don’t activate it)
We need to change all FQDN that Exchange uses for different Service now to the SAME FQDN the SINGLE Domain Cert runs on.
FQDN Single Domain Certificate was ordered for: async.customer.ch
OLD Entry in Exchange somewhere:
https://async.cutsomer.local/OAB
NEW:
Analyze the values you need to change by Powershell
- Read the Values (WAS) from Powershell Exchange for The things below and note them DOWN on a documentation
- Adapt the VALUES after term SET NEW with your new FQDN https://mynameiwant.mycustomerdomainexternal.ch/
————————————————————————————————————————————-
CHANGE1
get-ClientAccessServer | fl Identity,AutodiscoverServiceInternalUri
WAS:
Identity : CAS1
AutoDiscoverServiceInternalUri : https://async.customer.local/Autodiscover/Autodiscover.xml
SET NEW:
Set-ClientAccessServer -Identity CAS1 -AutodiscoverServiceInternalUri
————————————————————————————————————————————-
CHANGE2
get-WebServicesVirtualDirectory | fl Identity, InternalUrl , ExternalUrl
WAS:
InternalUrl : https://cas1.customer.local/EWS/Exchange.asmx
ExternalUrl : https://mobile.customer.local/ews/exchange.asmx
SET NEW:
Set-WebServicesVirtualDirectory -Identity “CAS1\EWS (Default Web Site)” -InternalUrl https://async.customer.ch/EWS/Exchange.asmx
Set-WebServicesVirtualDirectory -Identity “CAS1\EWS (Default Web Site)” -ExternalUrl https://async.customer.ch/EWS/Exchange.asmx
————————————————————————————————————————————-
CHANGE3
get-OABVirtualDirectory | fl Identity, InternalUrl, ExternalUrl
WAS:
InternalUrl : http://cas1.customer.local/OAB
ExternalUrl : https://mobile.customer.local/OAB
SET NEW:
Set-OABVirtualDirectory -Identity “CAS1\OAB (Default Web Site)” -InternalUrl http://async.customer.ch/OAB
Set-OABVirtualDirectory -Identity “CAS1\OAB (Default Web Site)” -ExternalUrl http://async.customer.ch/OAB
————————————————————————————————————————————-
If you don’t have UTM Service (Unified Messaging leave that)
Change Values in Exchange 2010 GUI
Change all other things in Exchange 2010 GUI on the tabs below to corresponding values.
Some you may have changed above already. Check them twice.
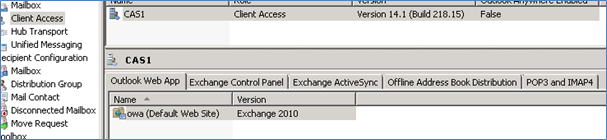
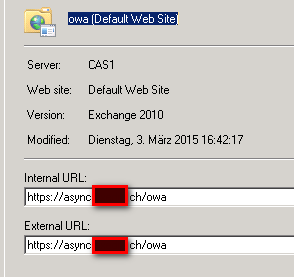
- Do this for all possible location Web app/Activesync/Offline etc.
- DO this for INTERNAL and EXTERNAL (Set the SAME value)
- Do not change AYNTHING behind the FQDN name as example
- AT the end Restart Exchange or do a CMD.exe then IISRESET
OLD:
https://async.cutsomer.local/OAB
NEW:
Activate the Certificate in Exchange 2010 GUI or Powershell and RESET IIS
Activate the new SINGLE Certificate in Exchange for IIS.
Get-exchangecertificate | fl
Get the GUID sample: 020564B683E9D540DA0DF20A
enable-exchangecertificate -identity 020562B683E5D540DA0DF20A -Services “IIS”
AT the end Restart Exchange:
CMD.exe then IISRESET
References:
SPLIT DNS, Windows Server 2008: The Definitive Guide
SPLIT DNS with ISA
http://www.isaserver.org/img/upl/isabokit/9dnssupport/9dnssupport.htm#_Toc63649957
Exchange PRO
Main Technet Link
http://support.microsoft.com/kb/940726/en-us


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.