“We once had a case where we needed to install a URL-Rewrite Module in IIS CAS 2010 to submit more information to the Rapid7 Solution. (This was during a time before all the monthly leaks for 2013/2016/2019 came up, pushing all customers towards M365, and it was unclear what the module would do inside Exchange, etc.) We had previously used URL-Rewrite for a web server at our ISP, but it did not work the same way on IIS. On IIS, you have to uninstall IIS Sites and reinstall with an EXE, which runs 100% PowerShell. The CAS was behind a commercial KEMP Load Balancer HA.
I recently encountered a similar case on one of my private Windows IIS web servers, where I had to tunnel through several active components.
Solution: How to Determine the Source IP when your IIS Web Server is behind a KEMP Load Balancer.”
I’ve corrected the spelling, grammar, and punctuation errors to make the text more readable and professional.Schema: “WAN”—–“FW1″—”FW2”—“KEMP” (back: 192.168.185.105)—–(front: 192.168.151.70)”WEB SERVER/MS/IIS” Info you have BEFORE in IIS Logfiles (You do not see the Source IP in IIS Logfiles) 2023-01-21 19:08:35 W3SVC2 web 192.168.185.105 GET /image.axd picture=041014_0945_WSUSWindows1.png 443 – 192.168.151.70 HTTP/1.1 Mozilla/5.0+(Windows+NT+10.0;+Win64;+x64)+AppleWebKit/537.36+(KHTML,+like+Gecko)+Chrome/109.0.0.0+Safari/537.36+Edg/109.0.1518.61 – www.butsch.ch 200 0 0 8644 742 4 Solution Info you have after our change in IIS Logfiles (Source IP at end) 2023-01-21 19:46:28 W3SVC2 web 192.168.185.105 GET /category/APP-V.aspx – 80 – 192.168.151.70 HTTP/1.1 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10_15_7)+AppleWebKit/605.1.15+(KHTML,+like+Gecko)+Version/14.1+Safari/605.1.15 – – www.butsch.ch 404 0 0 23895 382 12 15.206.212.159 Go onto your KEMP/Also works with free community
Version:
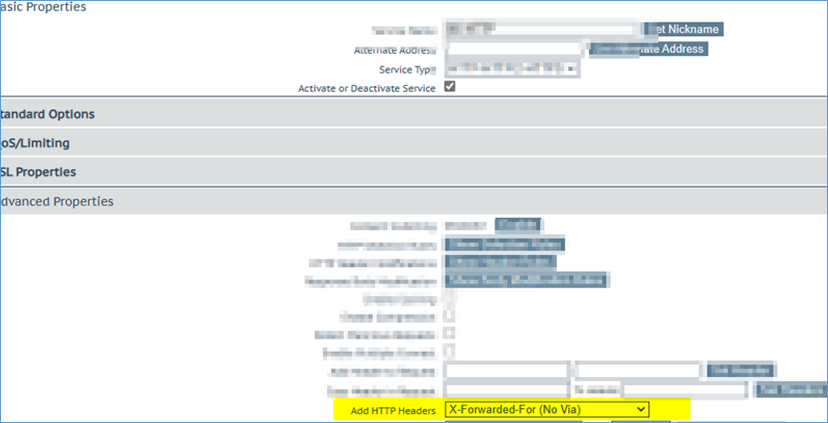
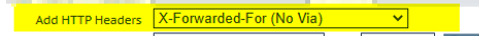
Select MODIFY Service; Under Advanced Properties change “Add HTTP Headers” to “X-Forwaded-For (No Via)” or try any other option and check on IIS side Logfiles what you see there.
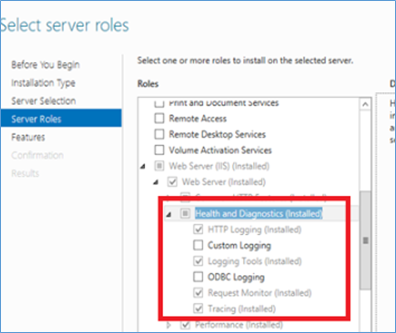
First make sure Logging in IIS is installed (If not).
Here is what to change in IIS if you have logging active:
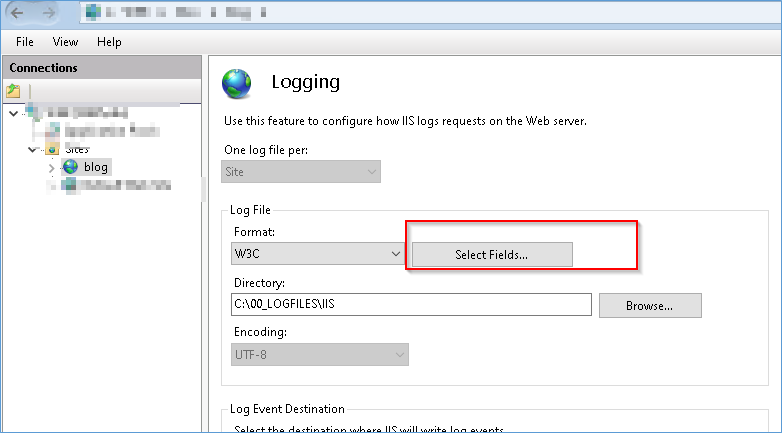
Change the LOGFILE Location to a Disk where you have space or monitor.
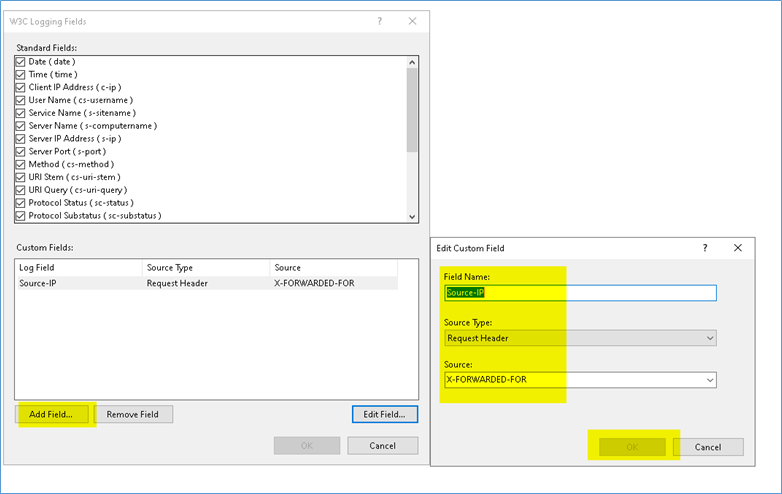
Source X-FORDWARDED-FOR that was the field you told him on the KEMP to include in any packet he sends back
Cmd (Elevated) IISRESET Or Restart Server You will see the Source-IP at the end of line: 2023-01-21 19:46:28 W3SVC2 web 192.168.185.105 GET /category/APP-V.aspx – 80 – 192.168.151.70 HTTP/1.1 Mozilla/5.0+(Macintosh;+Intel+Mac+OS+X+10_15_7)+AppleWebKit/605.1.15+(KHTML,+like+Gecko)+Version/14.1+Safari/605.1.15 – – www.butsch.ch 404 0 0 23895 382 12 15.206.212.159



 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.