

https://twitter.com/MSFT365Status/status
https://connectivity.office.com/status
Microsoft M36X has been scaling up its information system to address downtime, which is unsurprising considering the recent outages experienced in the past months.
Checking the Twitter Status M365 (https://twitter.com/MSFT365Status/status) in the morning is a good way to anticipate what to expect before opening your IT Support Ticket system. This allows you to make informed decisions, such as staying at home or securing the IT support door. You may also think in long term about studying art or other jobs beyond relying solely on the Cloud-O-Matic-Manager (COMM) duty. Maybe you find time to check SLA you have with your customers or with the company who runs your cloud.
Microsoft offers another tool that traces VPN-traffic or aM365 access worldwide, which can be used to identify existing cloud customers. Therefore, the next time your neighbour displays unusual Behavior, like throwing his BYOD laptop out of the window or being excessively loud in their home office, you can interactively investigate the reason using this tool
https://connectivity.office.com/status
So this enables you too see high traffic points. But there are several green points at private only location. Only private person rentals block as example.
You can also utilize a map provided by Microsoft, highlighting locations where a high volume of traffic is received from customers connected to Microsoft Teams, Exchange, SharePoint, and other services. This map serves as a useful resource to crosscheck whether an address corresponds to a private residence or a company complex. Furthermore, if a specific point on the map exhibits a large data volume, you can assume that the person or company:
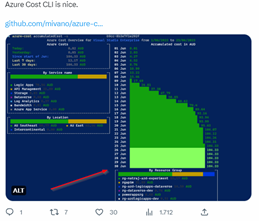
- Has implemented a split/non-split (FULL) VPN policy and may be downloading movies/warez from onedrive? He does not understand that everything he does private on his business laptop or his BYOD-enterprise-integrated-somehow may route all traffic to his employer (firm) and in this case straight through Microsoft Services somehow? On-premise you you took him down or took away his laptop toy. In the cloud you expect a really fat Express Route bill at the end of the month. You can even realtime see the Cloud cost in CLI/PS Microsoft told this week. That is a real neat tool you can see your Azure cost exploding in real time for your developers who profit from scalability as they always said.
b) Is using plain Microsoft Windows Defender ATP and lacks robust commercial enterprise endpoint protection such as McAfee/Trellix. In such cases, there is a possibility that the endpoint is currently infected and vulnerable due to the high traffic flowing through M365 services. While this level of paranoia might not be common, it’s essential to ensure proper endpoint protection.
In the past, on-premise enterprise IT teams effectively managed similar challenges with great success. These aspects can be effectively addressed in on-premise enterprise IT environments, especially when supported by dedicated IT teams.
That guy at Ochsengartenweg in Switzerland, i know him. I am sure he does not know we can see when he works or not? Please note that respecting privacy and confidentiality is crucial when using tools and maps to gather information about individuals or companies.
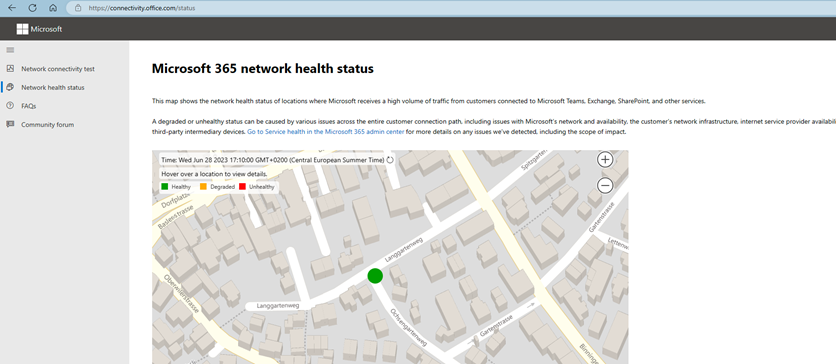
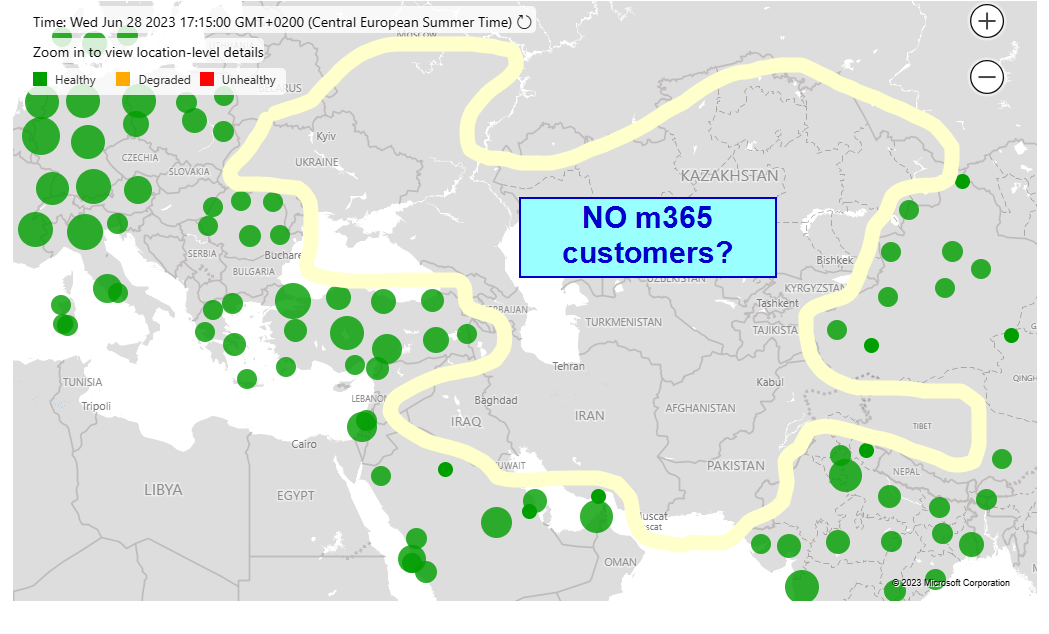
Microsoft 365 network health status
This map shows the network health status of locations where Microsoft receives a high volume of traffic from customers connected to Microsoft Teams, Exchange, SharePoint, and other services.
A degraded or unhealthy status can be caused by various issues across the entire customer connection path, including issues with Microsoft’s network and availability, the customer’s network infrastructure, internet service provider availability, and third-party intermediary devices. Go to Service health in the Microsoft 365 admin center for more details on any issues we’ve detected, including the scope of impact.
Region Basel
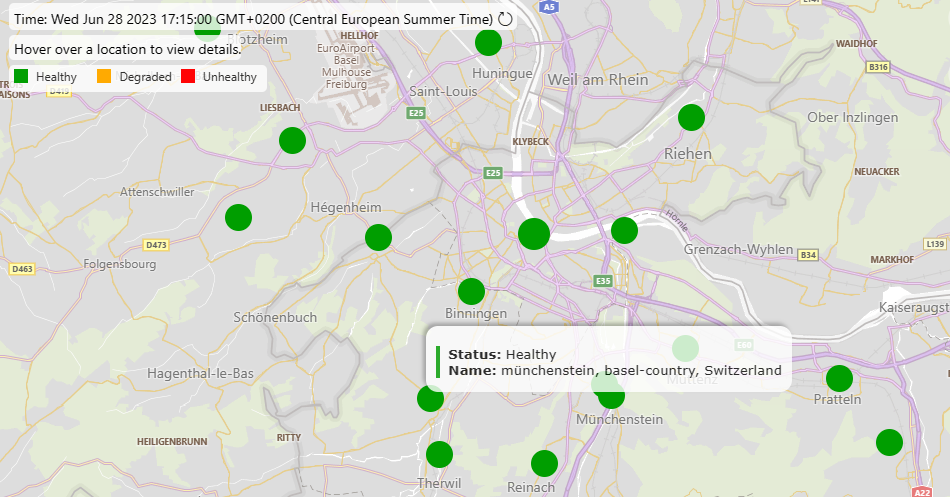
Not too many M365 users where “Borat” lives? Does BORAT use Google or TUX? Does he have an Amiga?
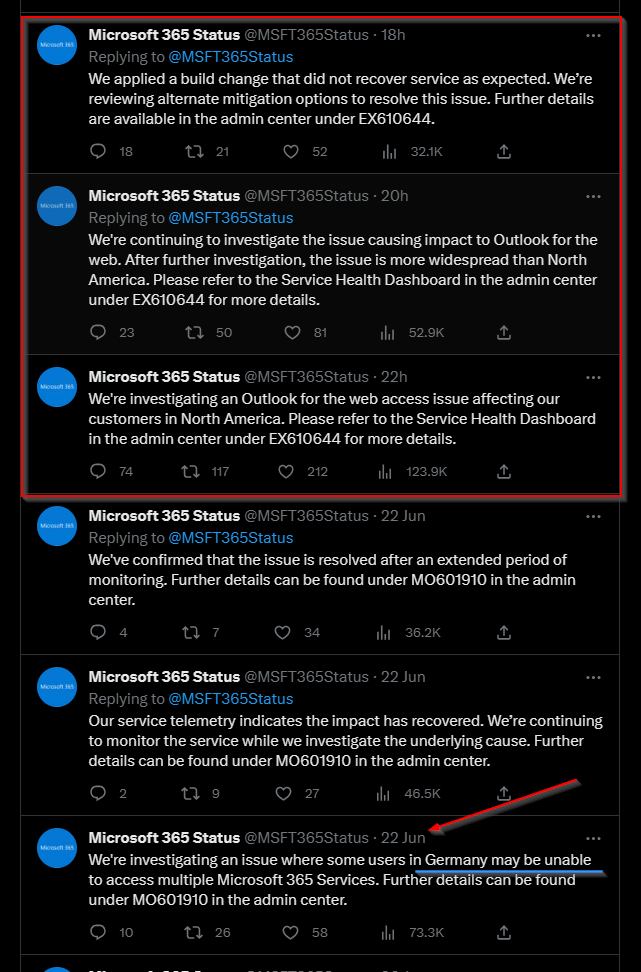
Some actual alerts these days:
Screenshot MS customer Portal 28.06.2023

22-28.06 from Twitter Microsoft 365 Status
VPN differences:
Full VPN, as opposed to split VPN, can often be a challenge when it comes to bandwidth. Here’s why:
1. Routing all traffic through the VPN: With a full VPN configuration, all network traffic from the user’s device is typically routed through the VPN tunnel. This means that even non-business-related internet traffic, such as browsing social media or streaming videos, will be redirected through the VPN server. As a result, it increases the overall bandwidth consumption.
2. Increased latency: The additional distance that data has to travel through the VPN server before reaching its destination can introduce latency or delay. This latency can impact real-time applications, such as video conferencing or online gaming, where responsiveness is crucial. The increased round-trip time can affect the user experience and degrade the overall performance.
3. VPN encryption overhead: VPNs use encryption to secure the data transmitted through the tunnel, which adds an additional layer of processing. This encryption process can increase the size of data packets, leading to larger bandwidth usage. The overhead caused by encryption can become more pronounced when dealing with high-volume data transfers or bandwidth-intensive activities.
4. Bottlenecks at the VPN server: Full VPN setups often involve funneling all traffic through a central VPN server or a limited number of servers. This concentration of traffic can lead to congestion and potential bottlenecks at the server level. As more users connect to the VPN and utilize the available bandwidth, it can impact the performance for all users connected to that server.
5. Limited VPN server capacity: VPN servers have finite resources, including processing power, memory, and network bandwidth. When multiple users connect to a VPN server simultaneously, especially during peak usage periods, the server’s capacity may be strained. This can result in reduced bandwidth availability for each user, affecting overall performance.
It’s important to note that while full VPNs can present challenges with bandwidth, they also provide enhanced security and privacy by encrypting all internet traffic. Organizations and individuals should consider the trade-offs between security and bandwidth requirements when choosing between full VPN and split VPN configurations.


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.