www.butsch.ch
Diese Anleitung beschreibt wie man einen HOTFIX auf einem MCAFEE EPO Server 4.5/4.6 integriert und alle Systeme oder eine bestimmte Gruppe verteilt. Als Beispiel den Patch/Hotfix vom 21.08.2012 für Mcafee VSE 8.8.
https://kc.mcafee.com/corporate/index?page=content&id=KB76004
DAT 6807/6808 Causing Issues with VSE 8.8.x
Inhalt
Distribute/Update an alle Endpoints im Netz 2
Distribute/Update PRO Untergruppe (z.B. an alle member Server) 3
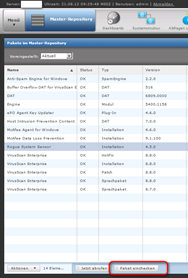
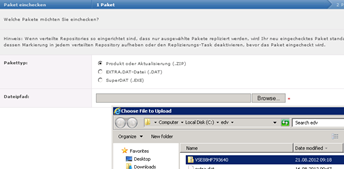
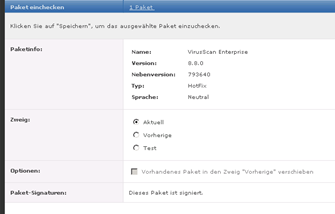
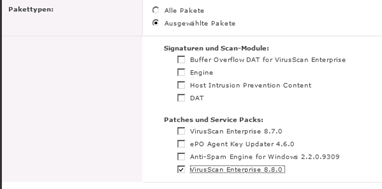
Hotfix Paket einchecken
Download the Hotfix from Mcafee: http://download.nai.com/products/hotfix/VSE88HF793640.Zip
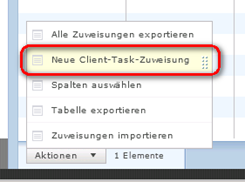
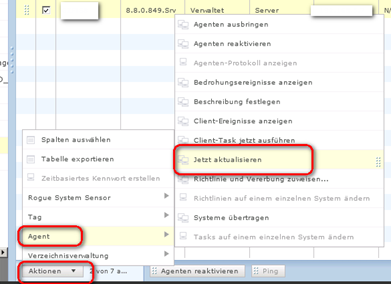
Distribute/Update an alle Endpoints im Netz
Now generate a task to distribute the Hotfix
Jetzt erstellen wir ein Task zum verteilen des Updates
Go to the “Root” of your EPO left
Zur “Eigenen Organisation” vom EPO gehen
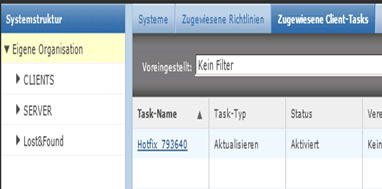
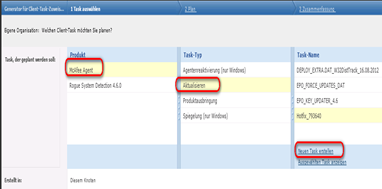
Mcafee Agent
Aktualisieren
Neuen Task Erstellen
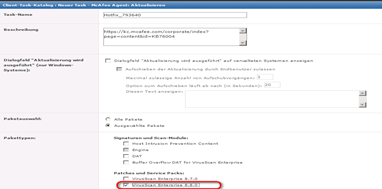
Call it “Hotfix_793640”
Den Task “Hotfix_793640” bennnen
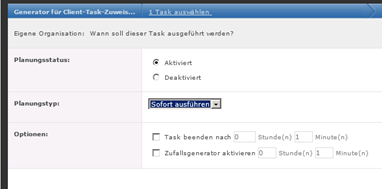
Distribute/Update PRO Untergruppe (z.B. an alle member Server)
Manchmal ist die Vererbung unterbrochen und man muss oder will dies den Update nur auf bestimmte Anzahl client verteilen.
You may also distribute per System group
Man kann es auch per System Struktur Gruppe verteilen
Mark the systems you want
Markiere die Systeme welche den Update erhalten sollen
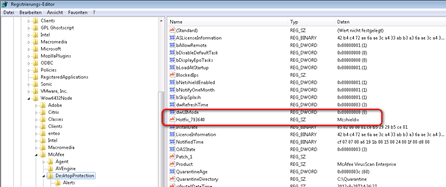
Kontrolle:
-
On the local system, check for the Hotfix_793640 entry in the appropriate registry location:
- 32-bit systems: HKEY_Local_Machine\Software\McAfee\DesktopProtection
- 64-bit systems: HKEY_Local_Machine\Software\Wow6432Node\McAfee\DesktopProtection
You can also check the machines which haven’t gotten the update with this SQL query on your EPO SQL DB:
SELECT ln.NodeName AS Hostname, pp.ProductVersion AS Version, pp.Hotfix AS Patch, ps.Value AS Hotfix
FROM EPOLeafNode AS ln INNER JOIN
EPOProductProperties AS pp ON ln.AutoID = pp.ParentID INNER JOIN
EPOProductSettings AS ps ON pp.AutoID = ps.ParentID
WHERE (ps.SettingName = ‘Fixes’) AND (ps.Value NOT LIKE ‘%793640%’)
ORDER BY hostname
Also for some Reason please Exclude following file for the Hotfix from Scanning. That means on the Default Rules for VSe 8.8 (Client Rules) Exclude that File from beeing controlled.
Once again Mcafee blocks their own Updates with their own products. It seems that one deaprtment is in California and the developers are in India….
C:\ProgramData\McAfee\Common Framework\Current\VIRUSCAN8800\HotFix\793781\0000\VSE88HF793781.exe
C:\ProgramData\McAfee\Common Framework\Current\VIRUSCAN8800\HotFix\793781\0000\Patch.log (This he can’t write)
| Name der Bedrohung: | Common – Standardschutz:Ändern von Dateien und Einstellungen des McAfee Common Management Agenten verhindern |
|---|---|
| Typ der Bedrohung: | access protection |
| Ausgeführte Aktion: | Schreiben verweigern |


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.