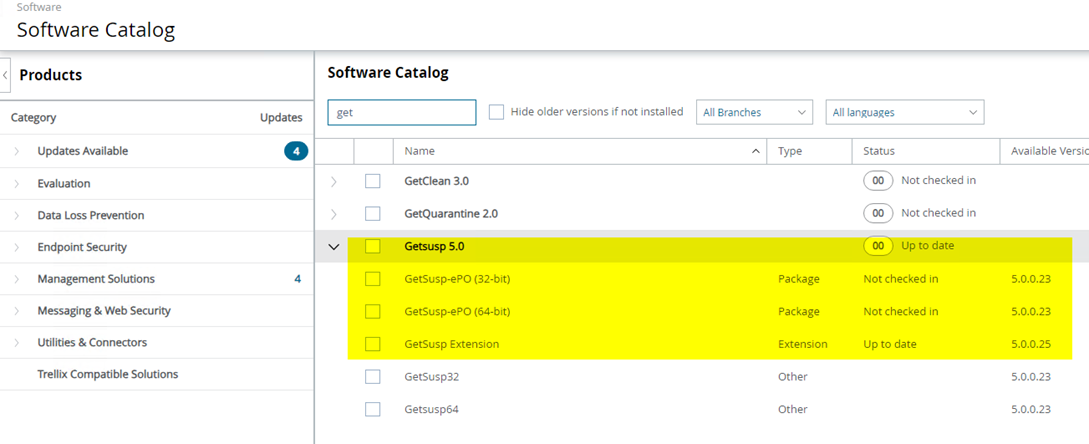
With EPO 5.10 on a fresh install, you have GetSusp.exe in both 32-bit and 64-bit versions in the Master if you perform an automatic product check-in.
You can easily run the small tool GETSUPS.exe (command line/GUI standalone scanner) via EPO. I am not sure if I missed it because I never use the product auto check in feature while installing EPO or if we tried once in the past in 2015 and it was not working as we wanted it. Now it seems to do fine or better.
https://www.butsch.ch/post/Mcafee-GETSUSP-(Stinger-V2)-free-Virus-Scan-HIPS/
You can manual use the freeware scanner tool via: https://www.trellix.com/downloads/free-tools/getsusp/
Nothing is free, and if it is, there is a reason behind it. McAfee/Trellix wants as many MD5 checksums worldwide of all files in their GTI cloud, especially from private users or dirty clients. Well, that’s just for the explanation of why something is free.
Why would you do that if you have the full ENS/CEB suite in place? Maybe if one module of ENS is in a corrupt Windows Installer state during migration, and you did not track old versions (due to another product disrupting your ENS uplift via EPO).
For the protection of McAfee developers: The deployment and upgrade of ENS via EPO is the best we have seen over the years regarding the deployment process, in comparison to ANY other enterprise deployment (Workplace Management) solution.
This is similar to getclean.exe, a command-line scanner with a GUI based on GTI. Maybe a good reference if you sometimes have too many exceptions in place because of performance or simply because you are told to exclude certain processes by the producer.
GETCLEAN.EXE = Diagnose and report FALSE before you ROLLOUT or activate ATP/DAC/IPS.
GETSUSP.EXE = Really a small compact offline scanner that uses GTI from Trellix, so you need WAN/Internet Access. In an Outbreak, Lockdown, Breakout, or whatever you call it when you are in trouble, make sure you have those WAN URLs open and all others closed until you know what goes on.
We think this is a cross-check tool or to find out if you excluded too many processes, paths, or certs with all products from McAfee/Trellix.
The interesting part is the Auto submit to Trellix with an E-Mail address where you COULD track the submit.
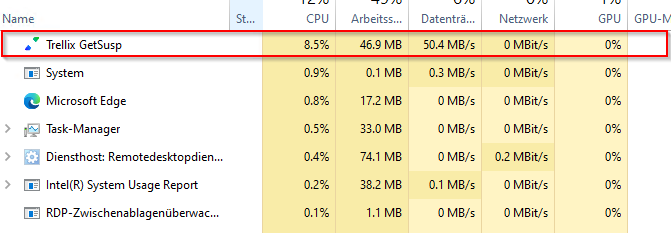
The software, if deployed by EPO TASK, comes as “Trellix getsups” on the client. On a 2020 HP client it eats around 10% CPU which looks very nice.
In EPO you find it here:

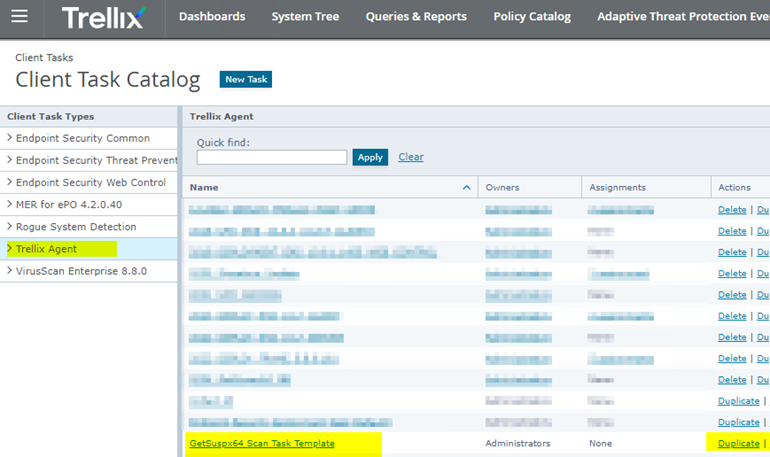
Now duplicate their sample Client Task aka JOB Deployment Task
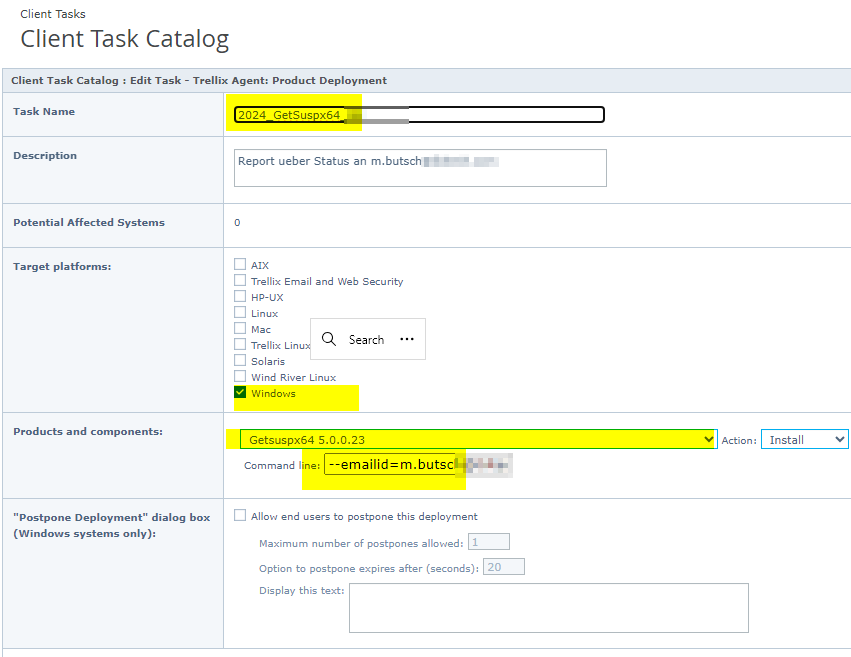
Trellix if you know? Your Docu does not tell us….
The only thing we currently are unsure with this tool is the flow of E-Mail. Will we get a inbound confirmation like with getclean.exe upload? And where is the E-Mail/SMTP Sent from? From the client via SMTP/Outlook which is blocked 99% or via the SMTP Server settings in EPO? Will update as soon as we trace or get info from Trellix on this.
“When” running as shown above with the –emailid= command line option WE DID NOT get any INFO back to EPO. I think it tries than and breaks or stalls if he can’t send E-Mail outside. Still unclear.
Options for the field command line (It is silent by default built in by version 5.x)
–offline
No automatic submission of GetSusp results.
–emailid=myemail@example.com
GetSusp submissions with an email address receive an acknowledgment with an item ID from Trellix for tracking purposes. This item ID can be used to follow up with support team.
–zippath=C:\GetSusp_Results
Location where GetSusp creates the ZIP with the results of the GetSusp scan.
–comment=
Leave a comment which is traceable in GetSusp reports. For example, a Service Request (SR) or customer internal incident number.
Run the CLIENT TASK/ Deployment JOB:
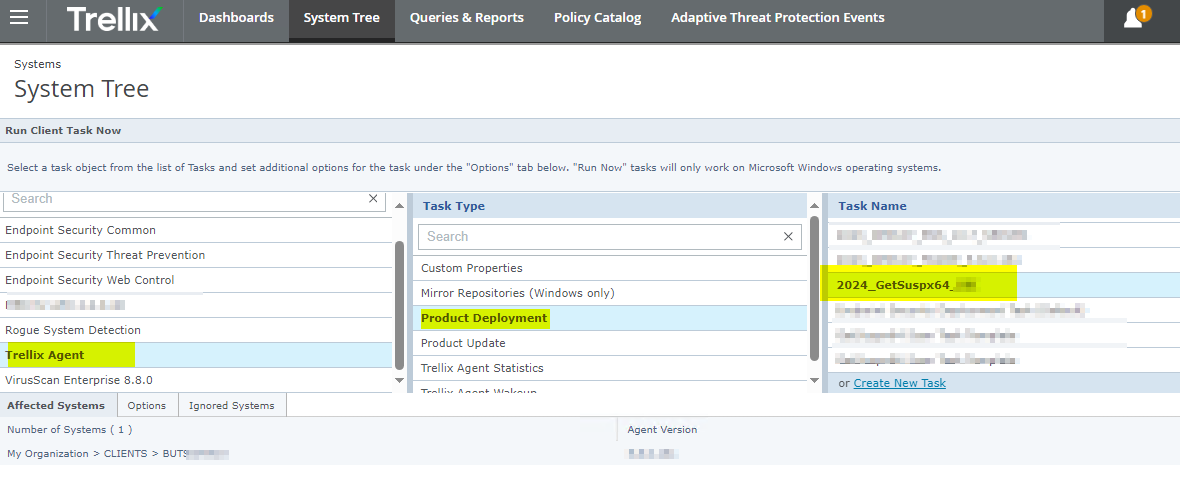
You checked in an EXTENSION so there is DASHBOARD
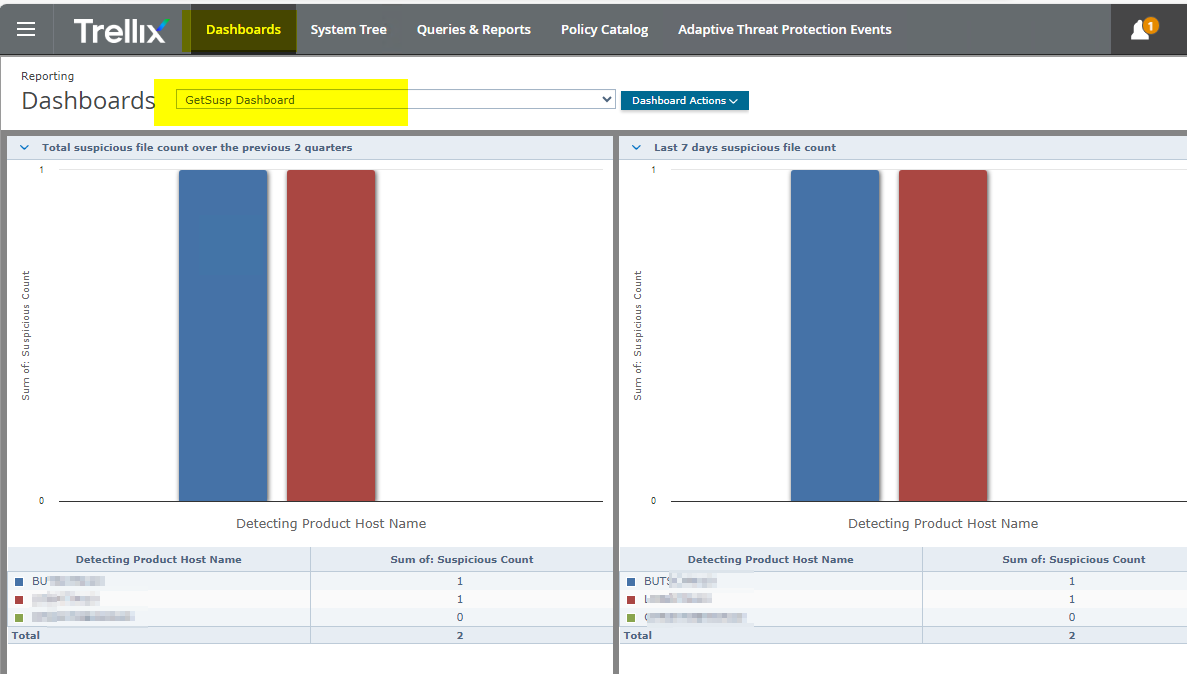
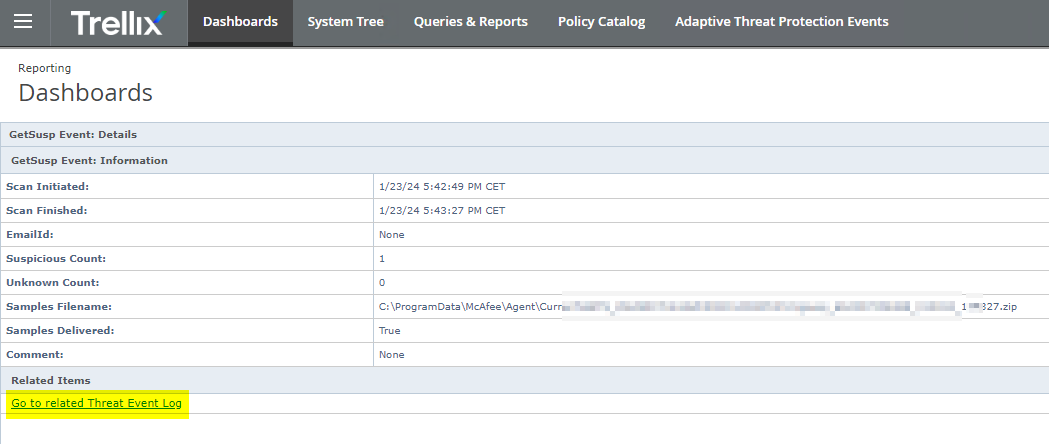
Maybe you step over some files that you included like Plugins for Outlook or for VOIP software which tends to hang when
Monitored by ATP Module DAC. Well hopefully the file will get now Auto submited to Trellix Labs / Mcafee Labs this way.
On a development machine wescanned it did report 2 file: The user is Angular development, Visual Studio 2019/2022, heavy coder with lots of other special tools. Looks good.
The only thing thinks is suspicious is Jetbrains c# enviroment.
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.CSharp.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.CSharp.Features.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.CSharp.Workspaces.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.Features.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.LanguageServer.Protocol.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.VisualBasic.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.VisualBasic.Features.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.VisualBasic.Workspaces.dll
C:\Program Files\JetBrains\JetBrains Rider 2022.2.4\lib\ReSharperHost\Microsoft.CodeAnalysis.Workspaces.dll
Second app he does not like:
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityDesigner2_2.3.1.2217_x64__3cqzy0nppv2rt\App\de\Serif.Affinity.resources.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityDesigner2_2.3.1.2217_x64__3cqzy0nppv2rt\App\de\Serif.Interop.Persona.resources.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityDesigner2_2.3.1.2217_x64__3cqzy0nppv2rt\App\de\Serif.Windows.resources.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityDesigner2_2.3.1.2217_x64__3cqzy0nppv2rt\App\Serif.Affinity.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityDesigner2_2.3.1.2217_x64__3cqzy0nppv2rt\App\Serif.Win32.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityDesigner2_2.3.1.2217_x64__3cqzy0nppv2rt\App\Serif.Windows.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityPublisher2_2.3.0.2165_x64__3cqzy0nppv2rt\App\de\Serif.Affinity.resources.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityPublisher2_2.3.0.2165_x64__3cqzy0nppv2rt\App\de\Serif.Interop.Persona.resources.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityPublisher2_2.3.0.2165_x64__3cqzy0nppv2rt\App\de\Serif.Windows.resources.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityPublisher2_2.3.0.2165_x64__3cqzy0nppv2rt\App\Serif.Affinity.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityPublisher2_2.3.0.2165_x64__3cqzy0nppv2rt\App\Serif.Win32.dll
C:\Program Files\WindowsApps\SerifEuropeLtd.AffinityPublisher2_2.3.0.2165_x64__3cqzy0nppv2rt\App\Serif.Windows.dll
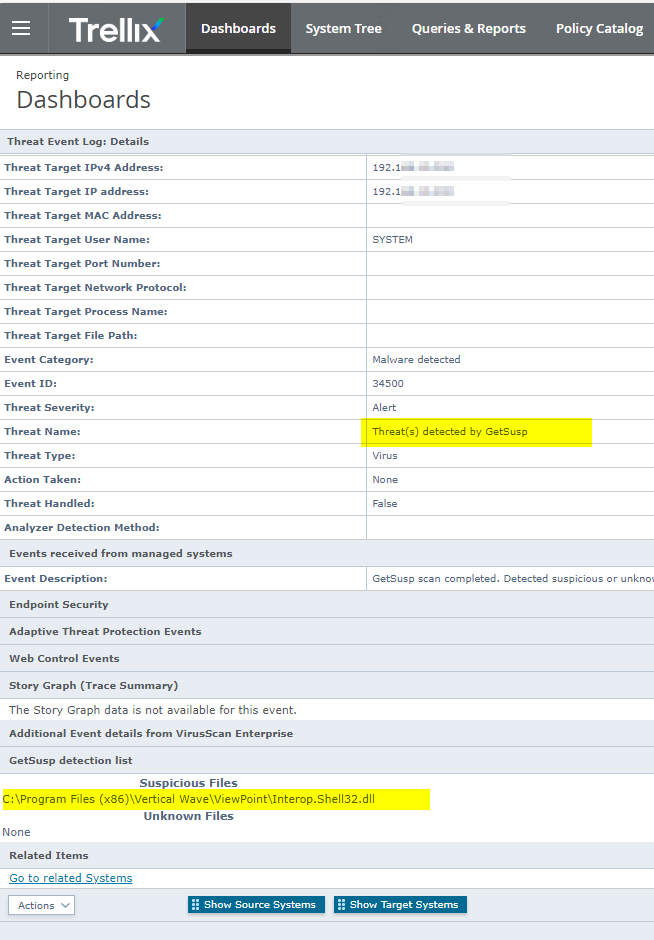
Some FAQ in here:
https://kcm.trellix.com/corporate/index?page=content&id=KB70405
Release:
https://kcm.trellix.com/corporate/index?page=content&id=KB91065&locale=en_US


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.