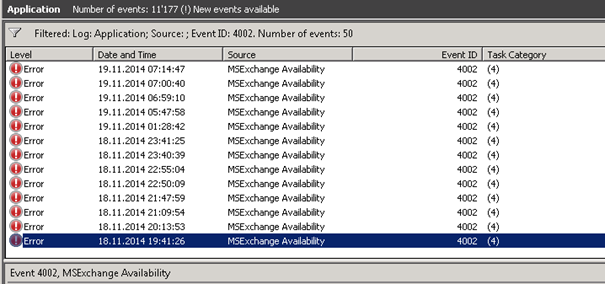
- Event 4002, Exchange 2010 CAS, MSExchange Availability
-
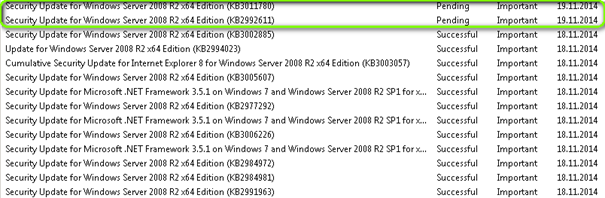
Microsoft KB 3011780 (V2) gets re-releases on 19.11.2014
-
Microsoft KB 2992611 (V3) gets re-releases on 19.11.2014 (V2) / 09.12.2014 (V3)
https://technet.microsoft.com/en-us/library/security/ms14-066.aspx
V1.0 (November 11, 2014): Bulletin published.
V2.0 (November 18, 2014): Bulletin revised to announce the reoffering of the 2992611 update to systems running Windows Server 2008 R2 and Windows Server 2012. The reoffering addresses known issues that a small number of customers experienced with the new TLS cipher suites that were included in the original release. Customers running Windows Server 2008 R2 or Windows Server 2012 who installed the 2992611 update prior to the November 18 reoffering should reapply the update. See Microsoft Knowledge Base Article 2992611 for more information.
V3.0 (December 9, 2014): Bulletin revised to announce the reoffering of the 2992611 update to systems running Windows Vista and Windows Server 2008. The reoffering addresses an issue in the original release. Customers running Windows Vista or Windows Server 2008 who installed the 2992611 update prior to the December 9 reoffering should reapply the update. See Microsoft Knowledge
2992611-V2 complete revert the things done before and does not fix the high risky security leak. There are too many Tird party components and even MS Products like Exchange WITH Plugins from Third Party which don’t work anymore.
I general the first patch could break all authentications against as example IIS, Exchange, Domain Controllers and Proxy Servers as example.
Remark:
The Event 4002, MSExchange Availability on Exchange 2010 has been there before [example May 2014] (Before release of 2992611). But we see it more often and just in the times range the patch was installed. This mainly in environments with Load Balancers and dedicated CAS-Server for as example Activesync and RSA. (Which is unsupported by MS still 😉
|
We have also seen Event 4002 related to OWA/IIS rsa-plugin on our RSA CAS Server |
|
The MS14-066 update also includes support for new SSL/TLS cipher suites. The new suites “…all operate in Galois/counter mode (GCM), and two of them offer perfect forward secrecy (PFS) by using DHE key exchange together with RSA authentication.” |
|
Process 2432: ProxyWebRequest CrossSite from S-1-1-0 to https://*.*.ch:443/ews/exchange.asmx failed. Caller SIDs: NetworkCredentials. The exception returned is Microsoft.Exchange.InfoWorker.Common.Availability.ProxyWebRequestProcessingException: System.InvalidOperationException: Client found response content type of ‘text/html;charset=utf-8’, but expected ‘text/xml’. The request failed with the error message: — <html><head><title>RSA SecurID PASSCODE Request</title> |
|
|
|
Event 4002 |
||||||||||||||||||||
|
||||||||||||||||||||
Bulletin Information:
=====================
MS14-068 – Critical
– https://technet.microsoft.com/library/security/ms14-068 (Link ist extern)
– Reason for Revision: V1.0 (November 18, 2014): Bulletin
published.
– Originally posted: November 18, 2014
– Updated: November 18, 2014
– Bulletin Severity Rating: Critical
– Version: 1.0
MS14-066 – Critical
– https://technet.microsoft.com/library/security/ms14-066 (Link ist extern)
– Reason for Revision: V2.0 (November 18, 2014): Bulletin revised
to announce the reoffering of the 2992611 update to systems
running Windows Server 2008 R2 and Windows Server 2012. The
reoffering addresses known issues that a small number of
customers experienced with the new TLS cipher suites that were
included in the original release. Customers running Windows
Server 2008 R2 or Windows Server 2012 who installed the 2992611
update prior to the November 18 reoffering should reapply the
update. See Microsoft Knowledge Base Article 2992611 for more
information.
– Originally posted: November 11, 2014
– Updated: November 18, 2014
– Bulletin Severity Rating: Critical
– Version: 2.0


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.