Antivirus Exclusion for NON Windows Defender
In the world of IT security, antivirus tools like Windows Defender are our go-to guardians against all sorts of threats. But sometimes, we need to make exceptions for certain stuff related to Microsoft Intune.
Now, here’s the deal (See end of this Blog entry below)
Windows Defender has this feature called Attack Surface Reduction (ASR), where it excludes specific executables, like the ones we’re talking about here. Some higher-ups and IT folks might see this as a handy feature.
For example, you can use batch commands to stop services like “Intelligenter Hintergrundübertragungsdienst” and “Windows Update.” This could be cool for IT folks who want more control over these services.
But, and it’s a big but, we need to be smart about it. Real hackers, like the ones in the Read Team Hacker community, might see these exclusions as opportunities to mess with our security. So, while we’re making life easier for ourselves, we’ve got to keep our guard up.
For more geeky details on this, check out the end of this blog.Unveiling Microsoft Intune Exclusions
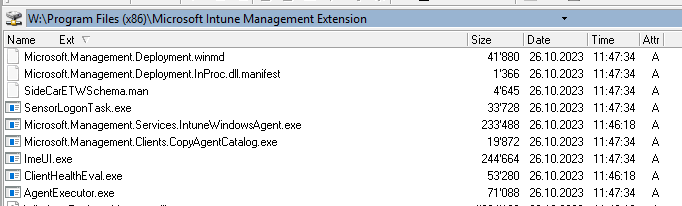
Processes: Within the realm of antivirus exclusions for Microsoft Intune, several pivotal processes warrant exemption from active scanning. These processes are integral to the seamless functioning of Intune, contributing to an optimal management experience. Here are some noteworthy processes that might necessitate exclusion:
-
AgentExecutor.exe
An indispensable component of the Microsoft Intune Management Extension, tasked with executing various functions crucial to Intune management.
-
ClientHealthEval.exe
Responsible for evaluating the health of the Intune client, ensuring adherence to required compliance standards.
-
ImeUI.exe
The Intune Management Extension User Interface, handling user interface interactions associated with Intune.
-
Microsoft.Management.Clients.CopyAgentCatalog.exe
Manages the catalog of agents, facilitating smooth communication between the client and management services.
-
Microsoft.Management.Services.IntuneWindowsAgent.exe
The core agent executing Intune management services on Windows devices.
-
SensorLogonTask.exe
An essential task for logging on to the Intune sensor, a critical component for endpoint security.
Directories: Equally crucial are the directories where Intune stores vital data and logs. Excluding these directories from active antivirus scanning ensures uninterrupted Intune operations:
-
c:\ProgramData\Microsoft\IntuneManagementExtension\Logs
This directory hosts log files vital for troubleshooting and monitoring Intune Management Extension activities.
- c:\Windows\IMECache
- Associated with Input Method Editors (IME), this directory is relevant to the functioning of Intune. Excluding it from antivirus scans prevents potential interference with IME operations.
Antivirus Exclusion Risks
While antivirus exclusions are at times essential to maintain the efficiency and functionality of specific processes, it’s imperative to approach them cautiously due to associated risks:
- Security Vulnerabilities: Excluding processes and directories may introduce security vulnerabilities, providing potential openings for threats to exploit.
- Malicious Payloads: Attackers could leverage exclusions to inject malicious payloads into the marked safe zones, leading to compromises.
- Unintended Consequences: Exclusions might inadvertently impact system stability or performance, especially if not thoroughly considered and tested in the specific environment.
Best Practices for Antivirus Exclusions in Microsoft Intune
- Regular Review: Periodically review and update the list of exclusions based on changes in the Intune environment or security landscape.
- Test Environments: Conduct thorough testing in controlled environments before applying exclusions in a production setting to assess potential impacts.
- Documentation: Maintain detailed documentation of all exclusions, including reasons behind each exclusion and associated risks.
- Collaboration: Encourage collaboration between security and IT teams to ensure that exclusions align with security policies while meeting operational needs.
In conclusion, while antivirus exclusions for Microsoft Intune are sometimes necessary for optimal functionality, a thoughtful and well-documented approach is crucial. Understanding the processes and directories involved, along with regular reviews and testing, can help strike the right balance between security and operational efficiency in the ever-evolving landscape of IT security.
An example for Mcafee/Trellix ENS 10.7 for the Directory. Keep in mind that you can exclude by process with MD5 checksumm with the ENS products at other parts and the main goal would be to exlude the process with MD5. However you would then re-check each release of Intunes Agent. If you use TIE/ATP Server from Trellix you could automate that process but thats a bigger price class and more complex.
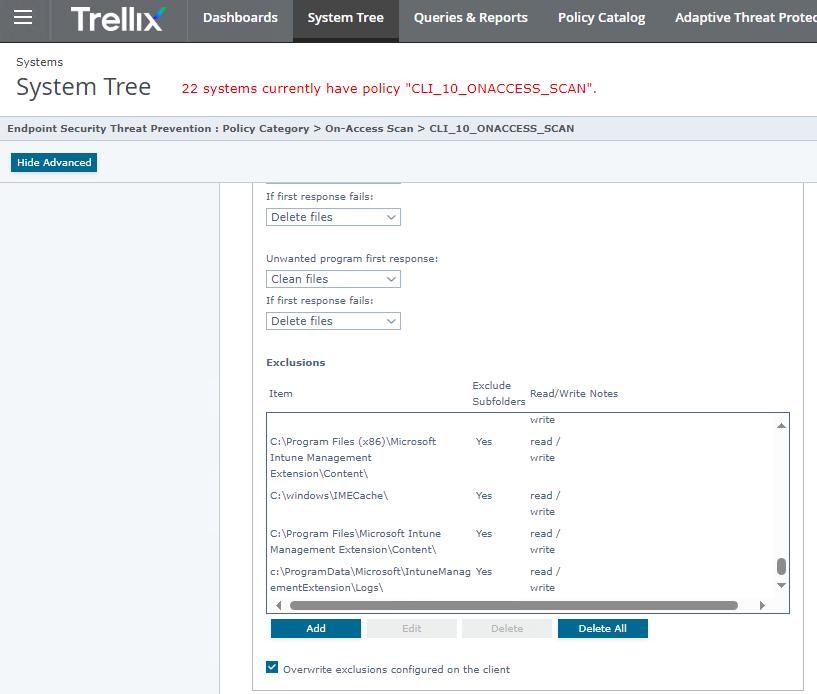
For SBS/KMU smaller shops we recommend to submit the files/exe/dll to Trellix GTI with getclean.exe
https://kcm.trellix.com/corporate/index?page=content&id=KB73044
After your you scan and send the EX/DLL to Trellix (Upload) you will get a report later.

At first these executables are already hardcoded excluded as exmaple in Windows Defender ASR. Some managers and IT may think this comey handy. Also Read Team Hacker and real Hackers think this is nice because they open security widely. You can read more about theis part at the of this bloig entry.
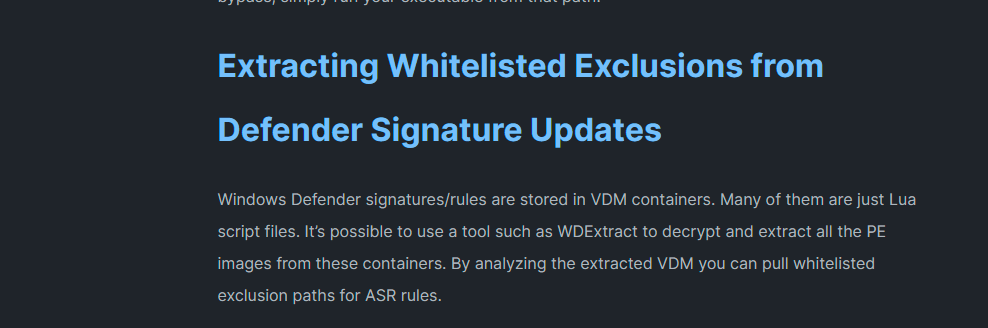
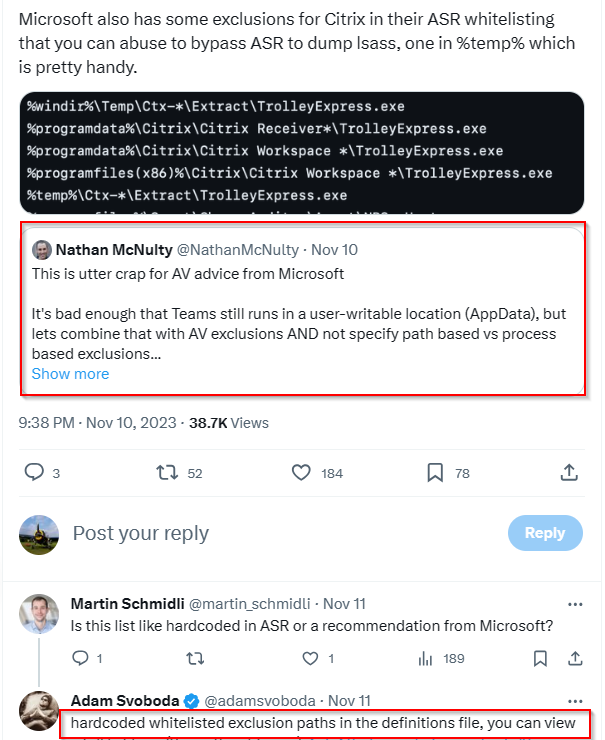
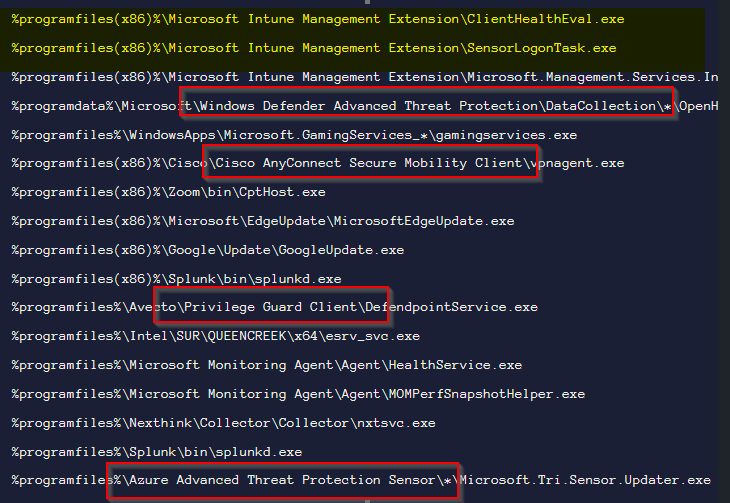
Source last screenshots are from X, Twitter and Adams Blog


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.