12.05.2017 Urgent Release FRIDAY, Wana Decrypt0r | Wana Decryptor | WanaDecryptor@.exe
https://kc.mcafee.com/corporate/index?page=content&id=KB89335
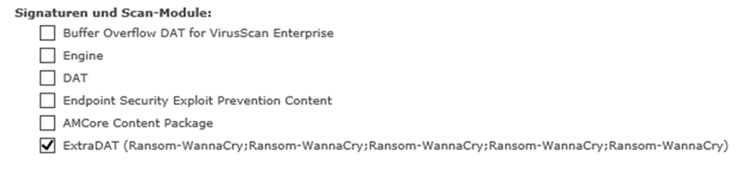
McAfee is aware that several customers are impacted by a new ransomware. Ransom-WannaCry (also known as WannaCry, WCry, WanaCrypt and WanaCrypt0r) is encrypting files with the .wnry, .wcry, .wncry, and .wncryt extensions. Encryption is occurring on the local host and across open SMB shares. Impacted systems might also show a blue screen upon system reboot.
https://kc.mcafee.com/corporate/index?page=content&id=KB89335
McAfee Client ENS 10.5.1 how to include the EXTRA.DAT (Extradat.zip) against the WannaCry Ransomware
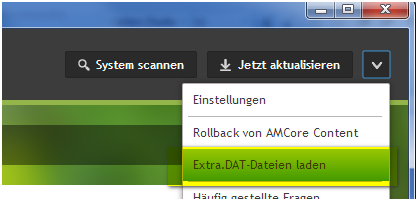
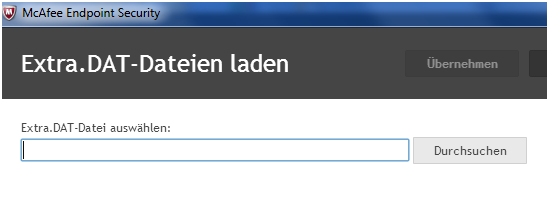
Unpack the EXTRA.ZIP to EXTRA.DAT
McAfee EPO: How to the DEPLOY the EXTRADAT in a GERMAN or ENGLISH EPO Server 5.X
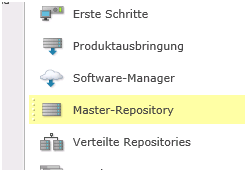
MENU > Master Repository
Unpack the EXTRA.ZIP to EXTRA.DAT
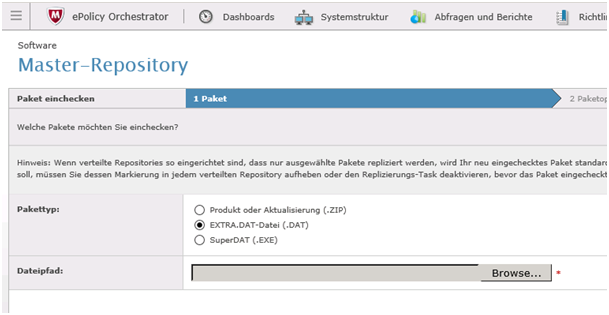
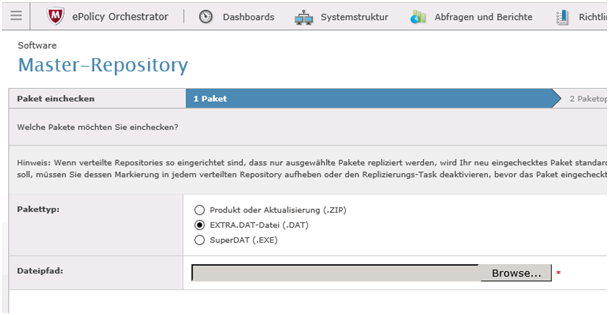
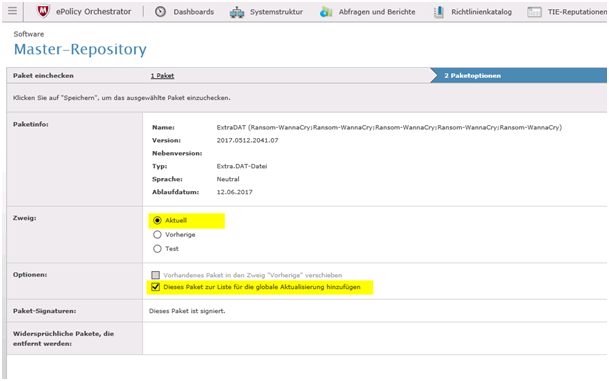
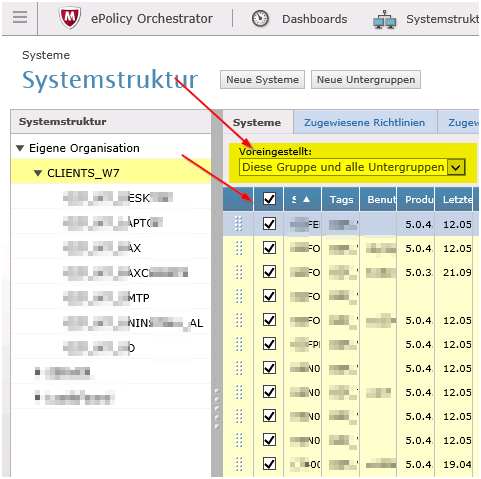
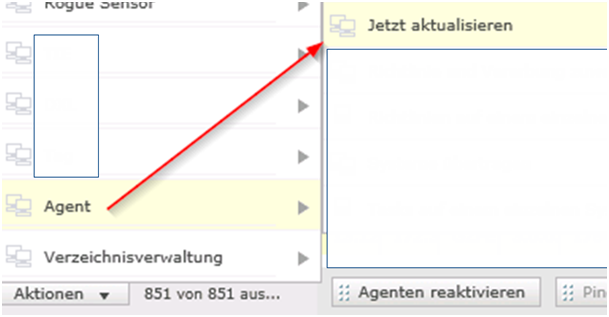
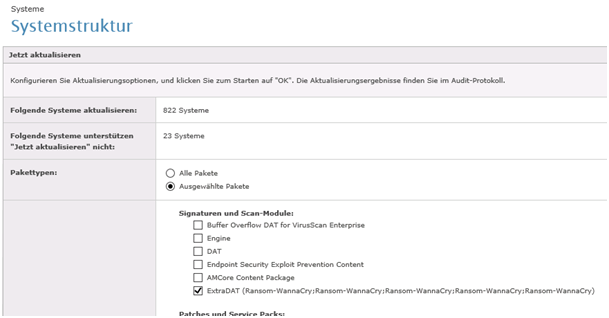
Make sure you check GLOBAL UPDATE. Above mentioned steps with UPDATE NOW do the same. Choose both ways to be 100% sure it done!
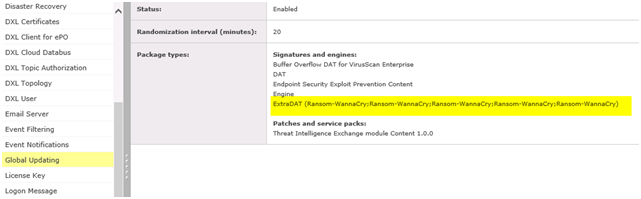
McAfee is aware of a new variant of ransomware that has been detected in corporate environments. Threat Name: Ransom-WannaCry (also known as WCry, WanaCrypt and WanaCrypt0r).
This article will be updated as additional information is available. Please continue to monitor this document for updates.
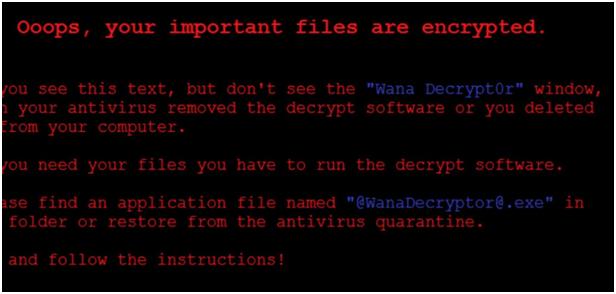
Files are encrypted with the .wnry, .wcry, .wncry, and .wncryt extension. End users see a screen with a ransom message.
-
End users see the following Ransom-WannaCry Desktop Background:
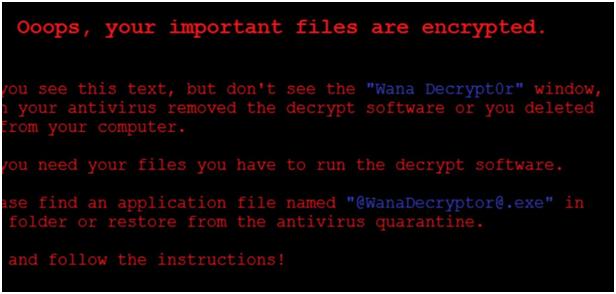
- On restarting, impacted machines have a blue screen error and cannot start.
- Encryption seen on local host and open SMB shares. IMPORTANT: Customers should immediately install the Critical Microsoft Patch MS17-010, to prevent SMB shares from becoming encrypted: https://technet.microsoft.com/en-us/library/security/ms17-010.aspx.
BUTSCH > Be CAREFULL with those VSE and ENS rules. DO NOT under any circumstance FORGET the SUBRULES! You would/will block all files otherwise! In newer Version you cant SAVE the rule then
VirusScan Enterprise (VSE) and Endpoint Security (ENS) Access Protection Proactive Measures
NOTE: The VSE and ENS Access Protection rules will prevent creation of the .WNRY file. This rule prevents the encryption routine, which is where one will see encrypted files that contain a .WNCRYT, .WNCRY and/or .WCRY extension. By implementing the block against .WRNY, other blocks are not necessary for the encrypted file types.
Use VSE Access Protection rules:
Rule1:
Rule Type: Registry Blocking Rule
Process to include: *
Registry key or value to protect: HKLM – /Software/WanaCrypt0r
Registry key or value p protect: Key
File actions to prevent: Create key or value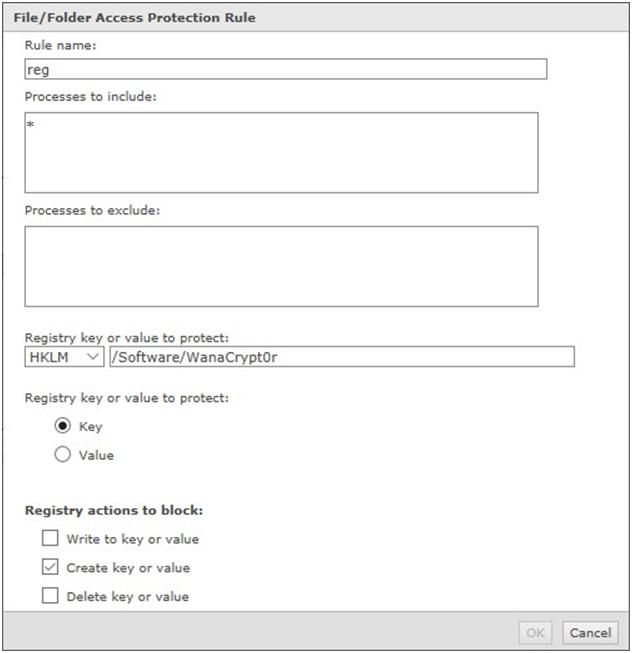
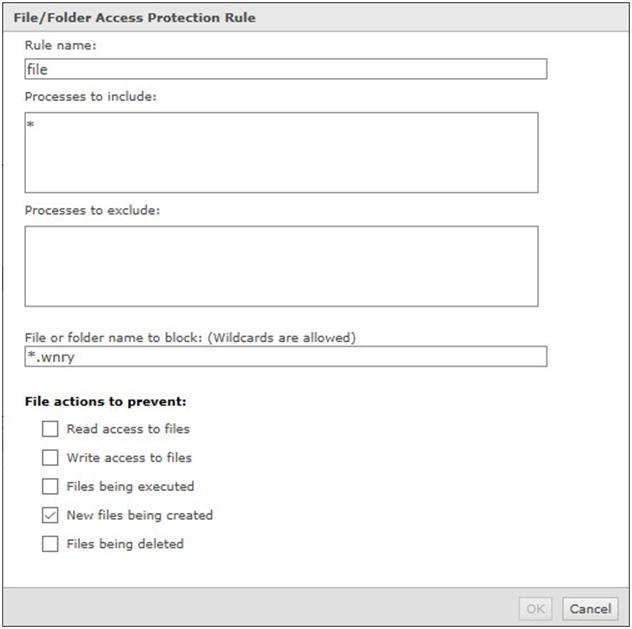
Rule2:
Rule Type: File/Folder Blocking Rule
Process to include: *
File or folder name to block: *.wnry
File actions to prevent: New files being created
Use ENS Access Protection rules:
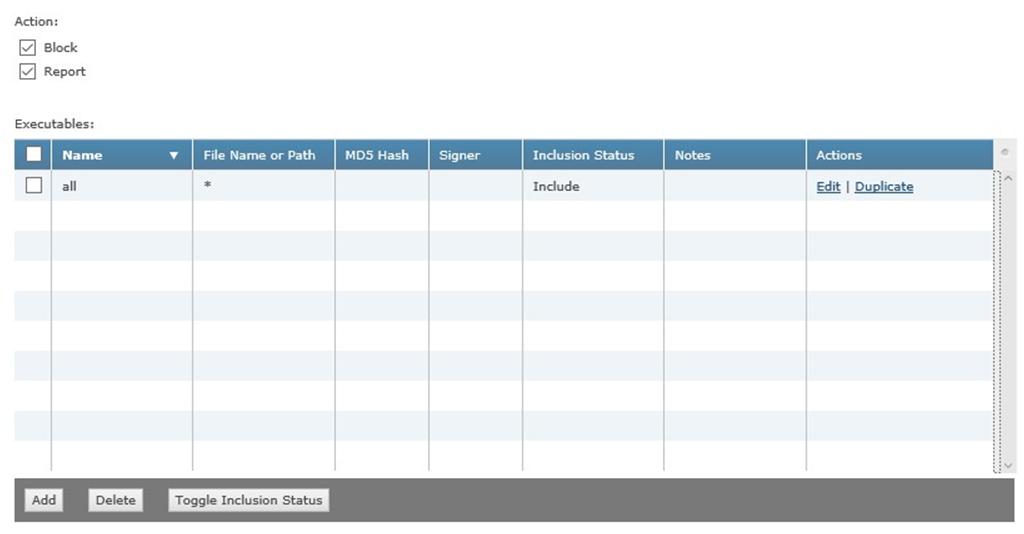
Rule1:
Executable1:
Inclusion: Include
File Name or Path: *
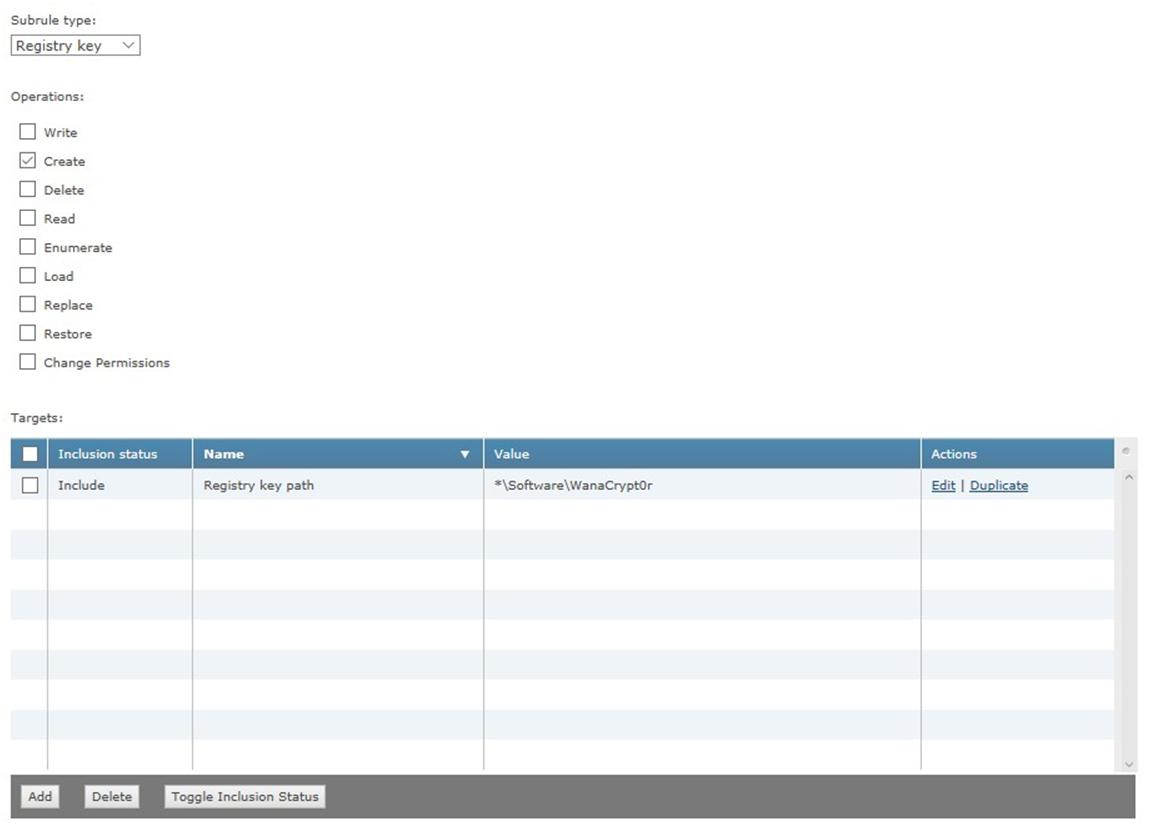
SubRule1:
SubRule Type: Registry key
Operations: Create
Target1:
Inclusion: Include
File, folder name, or file path: *\Software\WanaCrypt0r
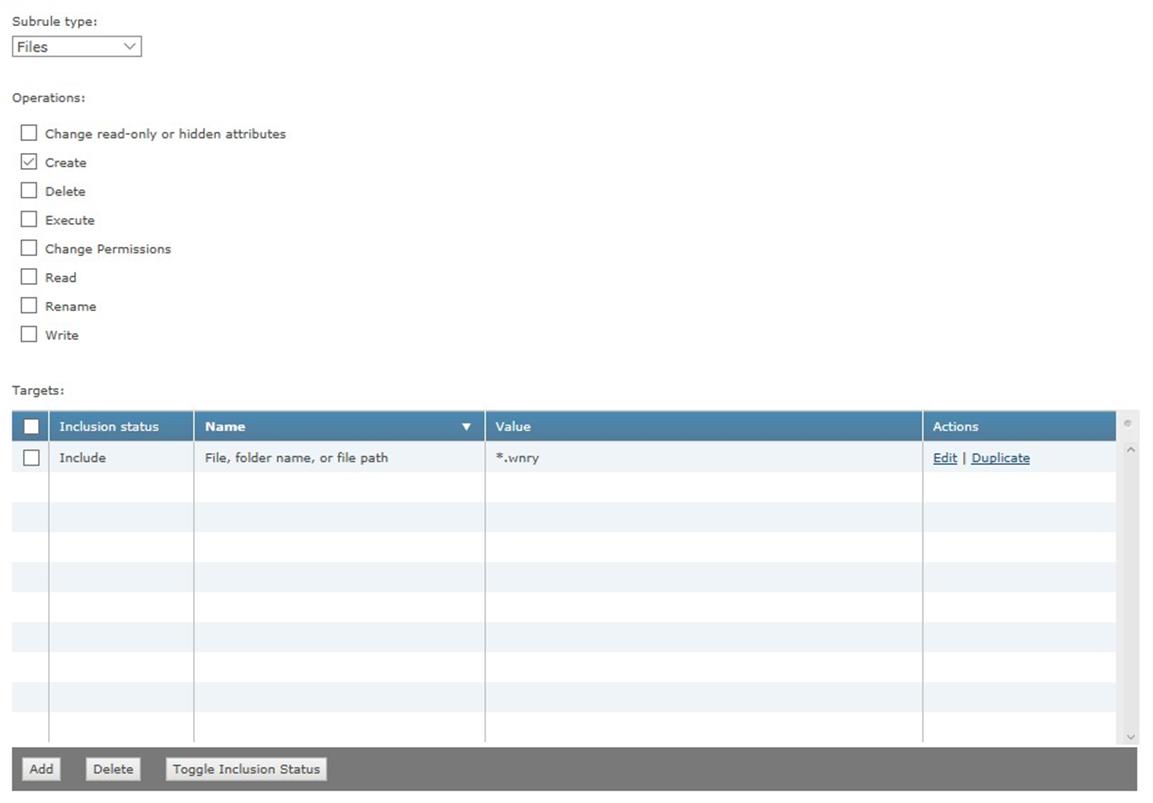
SubRule2:
SubRule Type: Files
Operations: Create
Target1:
Inclusion: Include
File, folder name, or file path: *.wnry
Please continue to return to this page for the latest updates.
Related Information
KB50642 – How to apply an Extra.DAT locally for VirusScan Enterprise 8.x
KB67602 – How to manually check in and deploy an Extra.DAT through ePolicy Orchestrator
Attachment
Malware, Ransomware, Virus, Hospital, Healthcare, Trojaner, Switzerland, Schweiz, Suisse


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.
