Check if you are affected by the 11/2018 SSD Bitlocker Leak.
ADV180028 | Guidance for configuring BitLocker to enforce software encryption
Security Advisory, Published: 06.11.2018
Producer: Samsung and Crucial
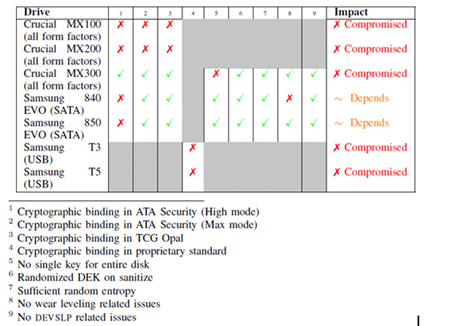
Affected models proof: Crucial MX100, MX200, MX300, Samsung EVO 840, 850, Samsung External USB T3/T5
There is a leak with certain SSD Hard disk (Solid-state) together with Microsoft Bitlocker. If you ONLY use software encryption you should not be affected.
There is a limited possibility then that the producer of the SSD disk still does encryption without feeding that info upwards to the OS but as we understood those are really a small size of disk.
Original text Microsoft in Advisory:
Microsoft is aware of reports of vulnerabilities in the hardware encryption of certain self-encrypting drives (SEDs). Customers concerned about this issue should consider using the software only encryption provided by BitLocker Drive Encryption.
On Windows computers with self-encrypting drives, BitLocker Drive Encryption manages encryption and will use hardware encryption by default. Administrators who want to force software encryption on computers with self-encrypting drives can accomplish this by deploying a Group Policy to override the default behavior. Windows will consult Group Policy to enforce software encryption only at the time of enabling BitLocker.
Advisory Microsoft
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/ADV180028
https://redmondmag.com/articles/2018/11/06/microsoft-ssd-security-advisory.aspx
Germans Ct Heise security Magazine
SC Magazine
https://www.scmagazineuk.com/ssd-encryption-security-failures-revealed-researchers/article/1498191
Samsung
https://www.samsung.com/semiconductor/minisite/ssd/support/consumer-notice/
Niederlande University
https://www.ru.nl/icis/news/recent_news/@1181122/radboud-university-researchers-discover-security/
https://www.ru.nl/publish/pages/909282/draft-paper.pdf
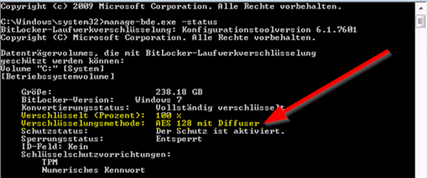
Here is how to check if you are affected:
Run elevated (Run as administrator)
Manage-bde.exe –status
This client is NOT affected since there is no Hardware Encryption:
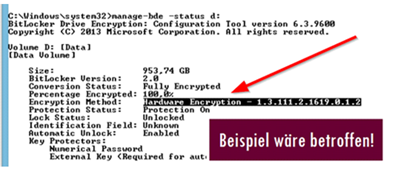
Possible affected client (Check further if SSD model is affected)


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.