Unable to migrate to Trellix Trellix Endpoint Security ENS 10.7.19 and ENS GUI crash with event 1000 (Update/migration/upgrade)
- mfeesp.exe crashing
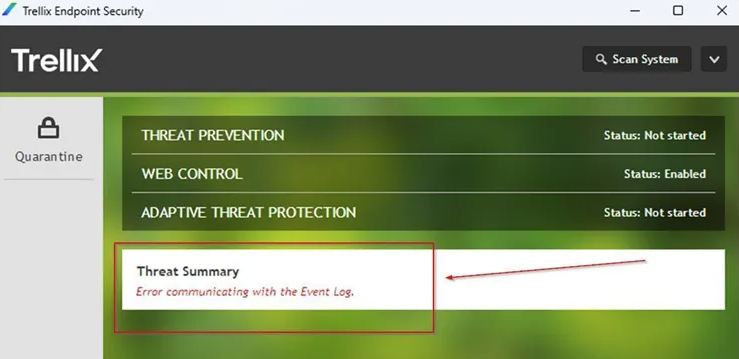
- GUI: Error communicating with the Event Log
- Application Event 1000 from MSVCP140.DLL, MSVCP140_1.DLL,MSVCP140_2.DLL, MSVCP140_atomic_wait.dll or MSVCP140_codecvt_ids.DLL
Affected OS we have seen with error:
- Microsoft Windows W11 24H2
- Microsoft Server 2016
- Microsoft Server 2019 Terminal Server Citrix
UPDATE 07.01.2026 there are only workarounds and pre-checks. Trellix did not release another new of ENS suite version to date 07.01.2025 January 2026
There is a pre check where you can estimate how many updates WILL fail. There is another tool to index the machines which failed and try to repair them.
We have seen the Error with 10-2025 and 11-2025 patches so if source was/would have been an MS change it was not fixed with the 11-2025 patches
08.12.2025 UPDATE | Trellix supplied a help tool remdediate_ens.exe
If you have a case open, Trellix support can supply a tool remdediate_ens.exe to find the affected client or server.
- There is a EEDK Package you can load into Master Repro in your EPO
- You can then deploy the package with two options to a) Report back to EPO if affected b) Try to Fix the MS Runtime for you

09.12.2025 Feedback from our side from 3 affected customers:
- We had one W11 VM where we could solve it with the tool without reboot and reinstallation of ENS
- We had one add. W11 IT-Engineer DELL laptop machine where we could not solve it with the supplied help tool from Trellix (
- We had 4 W11 HP Desktop where we could not solve it (But instead of Manuel using End Removable Tool we used the EPO version the first time – We have never had to before!)
- We had two Server, one 2016 and one 2019 where we could fix it with the supplied help tool from Trellix
Faulting application path: C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe
Faulting module path: C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\MSVCP140.dll
In past years, we loved the deployment process with McAfee/Trellix ePO. We could deploy to hundreds, if not thousands, of servers, and it just worked. There were some issues along the way due to certificates, code signing, and the transition from McAfee to Trellix. But overall, this was one of the best deployment mechanisms I have ever seen. It was reliable, and we could sleep well knowing that updating three Windows Installer MSI packages on hundreds of servers would just work. That is a main reason we liked Trellix.
This seems to have changed with the release of ENS 10.7.19. If you migrate to the latest release that Trellix ships, you may run into problems.
Path to problem:
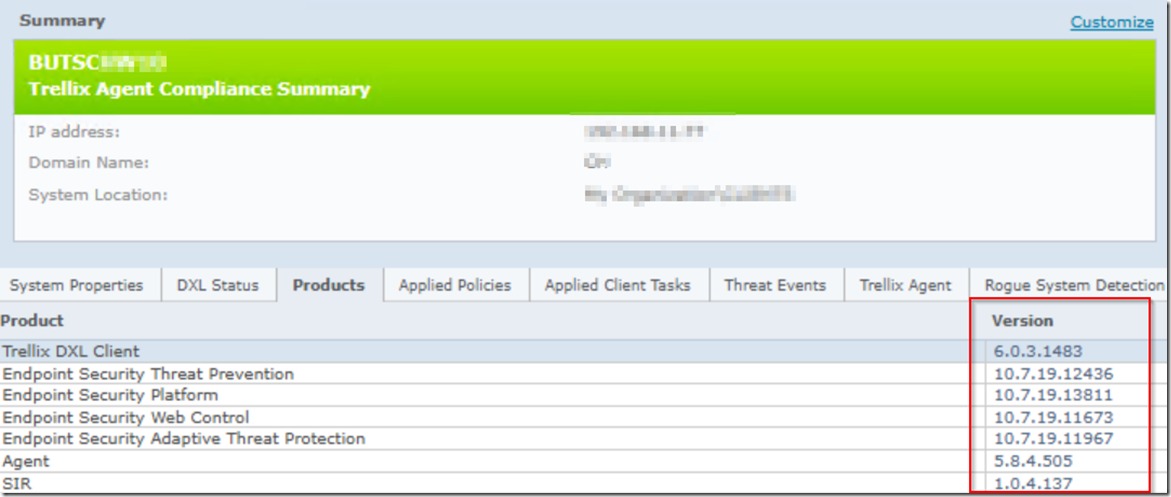
You want to update to latest ENS release:
Agent 5.8.4.505
Endpoint Security Threat Prevention 10.7.19.12436
Endpoint Security Platform 10.7.19.13811
Endpoint Security Web Control 10.7.19.11673
Endpoint Security Adaptive Threat Protection 10.7.19.11967
Trellix SIR inventory (This should not be the reason and helped us to find the Python machines quickly)
You migrated to the latest Trellix ENS 10.7.19 release as usual; the previous version was rolled out this summer.
- You integrate the new bundle, ENS 10.7.19, into ePO.
- You test deployment on a few clients or servers manually with a client task job.
- You update the deployment task to the new products.
- The agent picks up the migration process and updates each module to the latest release.
- You check ePO and think everything is fine > but it is absolutely not.
Problem:
On the ePO side, you see absolutely nothing after the task update, even though all chosen modules—like ENS Platform, Threat Protection, Web, ATP, or Firewall—are installed, and their versions are correct and up to date.
Affected OS:
We have seen the Problem on Windows 11 24H2 and Server 2016
Problem 1:
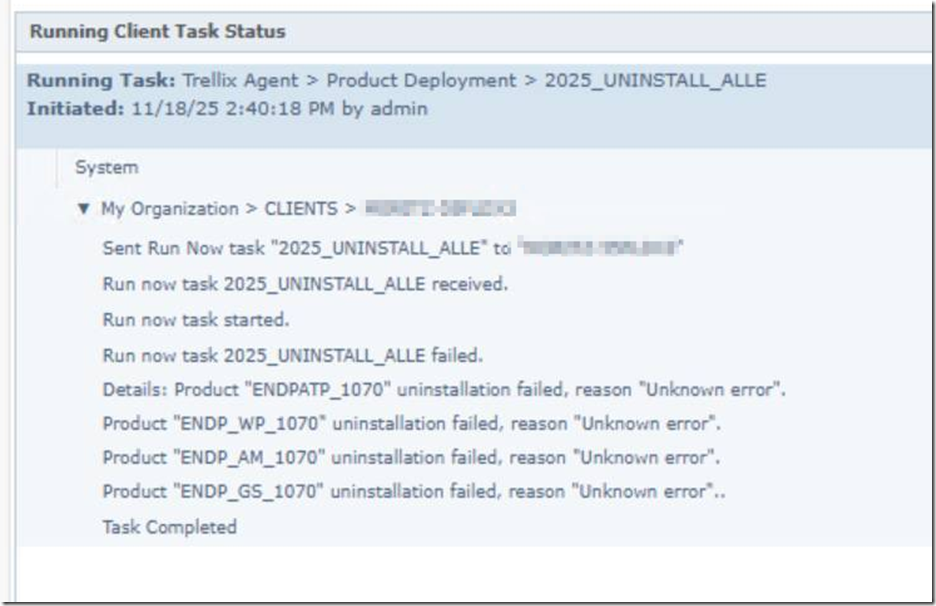
As per Trellix KB you should be able to Uninstall all Trellix, Reboot, Install the same version ENS 10.7.19 again
This worked for Server OS
it did not work for some W11 clients we had (Development) while it worked some normal IT machines
Security Problem 3:
On two machine the OAS On Access Scanner WAS Inactive and made handover to Windows Defender. So Defender came from Passive Mode to active. We tested with an EICAR file. Our SIEM put out an instant alarm because we capture the WD base things.
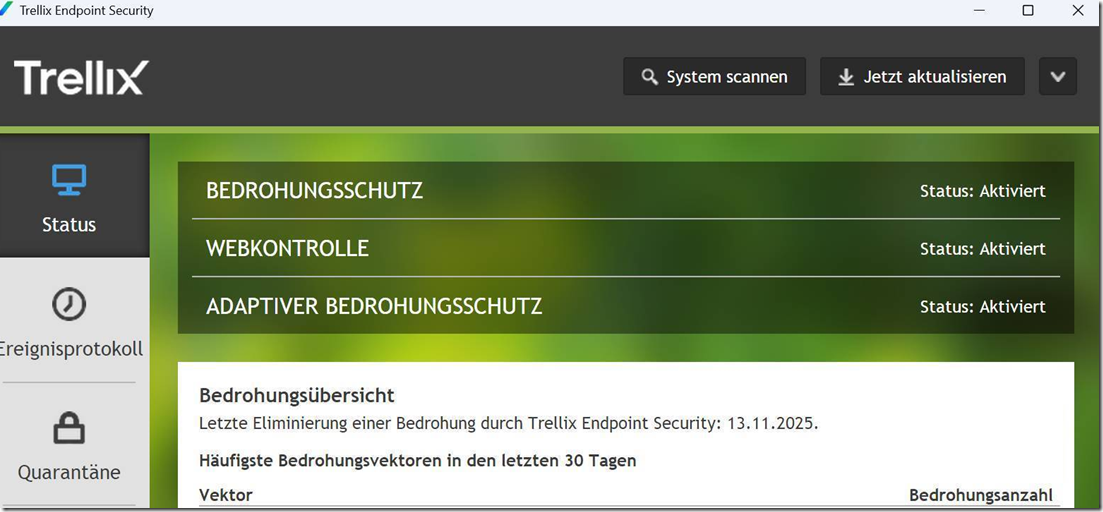
| If you open the Trellix ENS GUI you see “Error communicating with the Event Log” |
| Failed Look (BAD) affected
Normal Look: (GOOD) |
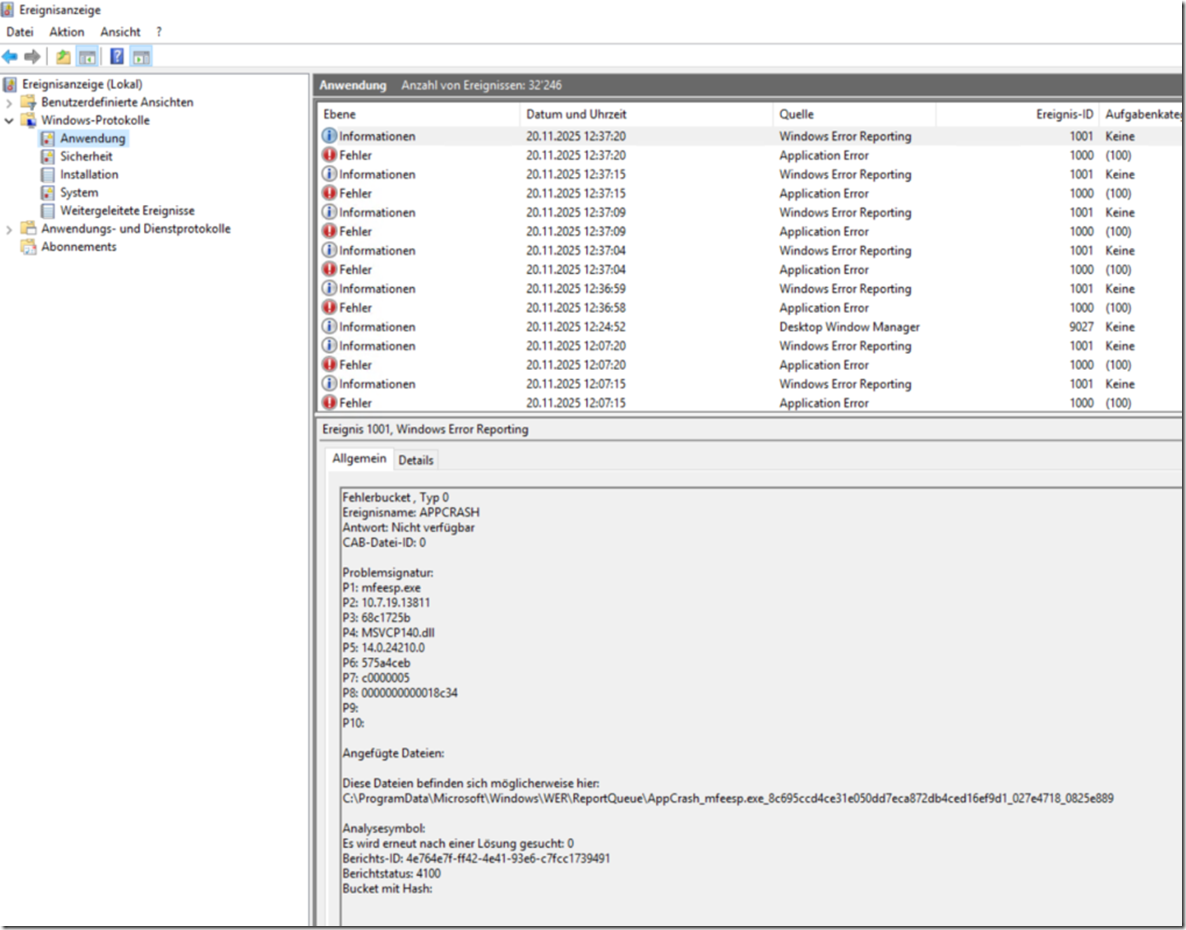
| You will see Event 1000 in the Event Viewer from a crash from mfeesp.exe |
| Faulting application name: mfeesp.exe, version: 10.7.19.13811, time stamp: 0x68c1725b Faulting module name: MSVCP140.dll, version: 14.0.24210.0, time stamp: 0x575a4ceb Exception code: 0xc0000005 Fault offset: 0x0000000000018c34 Faulting process id: 0x4854 Faulting application start time: 0x01dc523373c99b82 Faulting application path: C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe Faulting module path: C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\MSVCP140.dll Report Id: 6ec781cc-2feb-4616-938a-3b96260ebbc0 Faulting package full name: Faulting package-relative application ID: 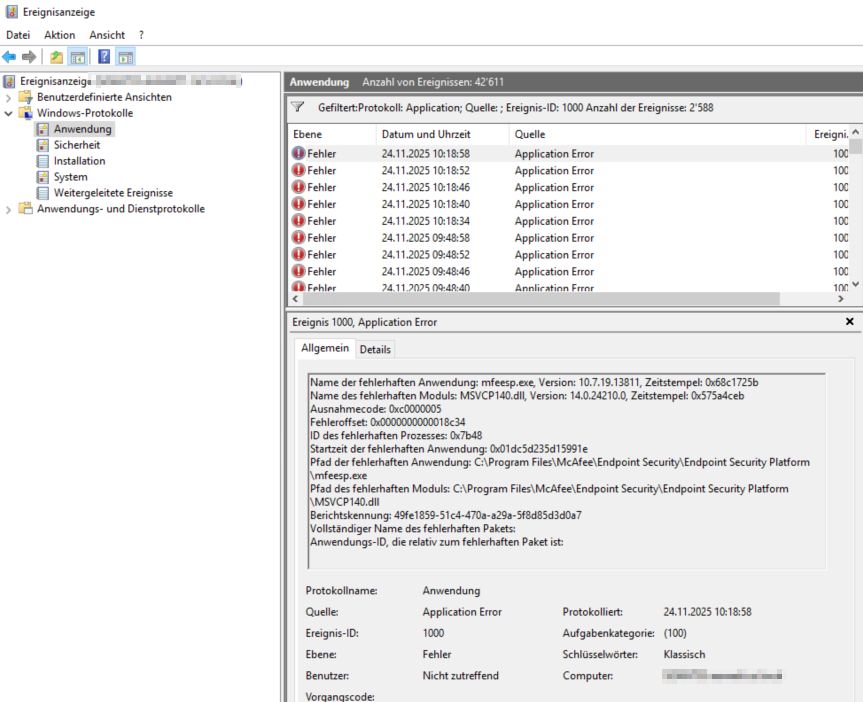 |
You are unable to deinstall the failed ENS version on the clients
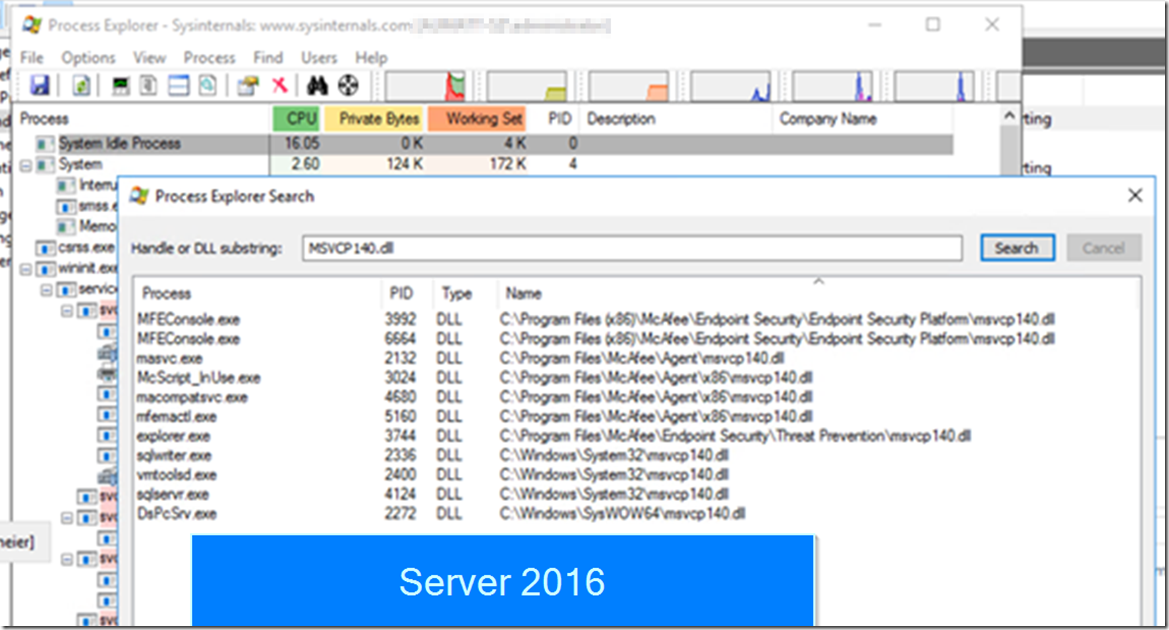
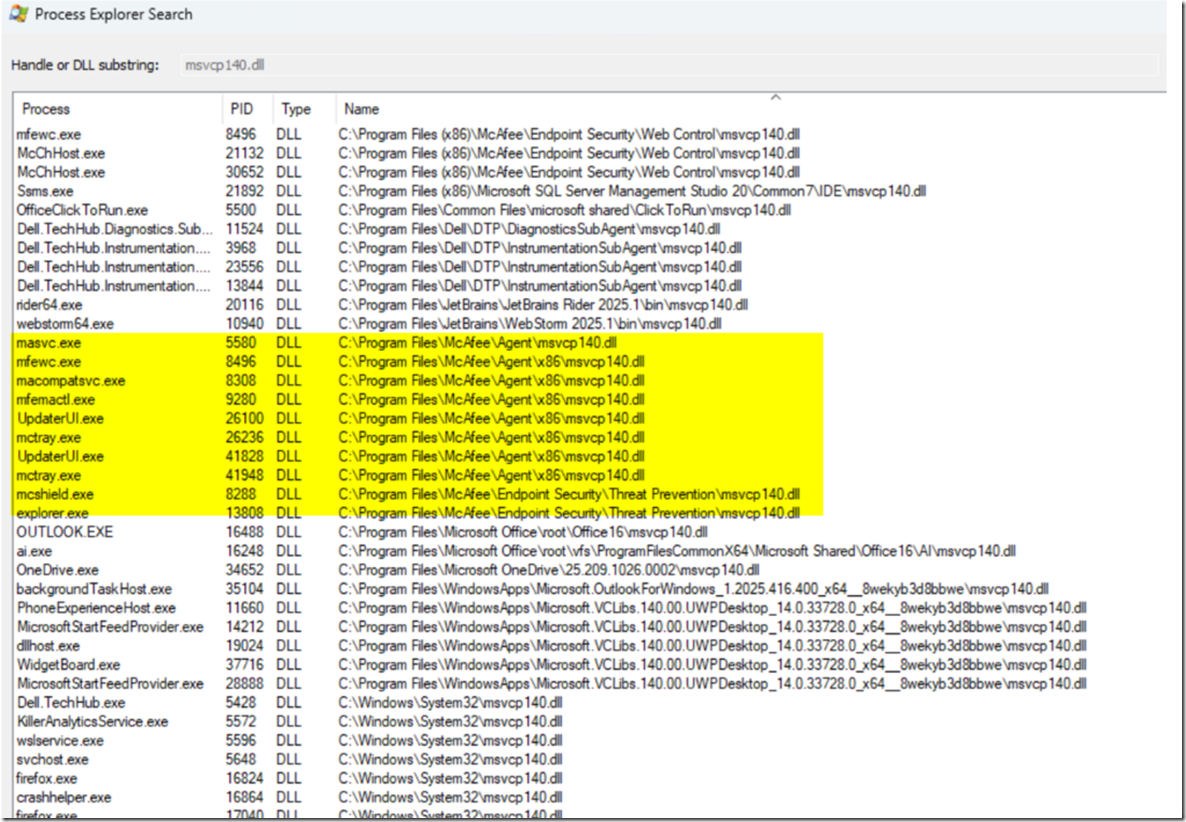
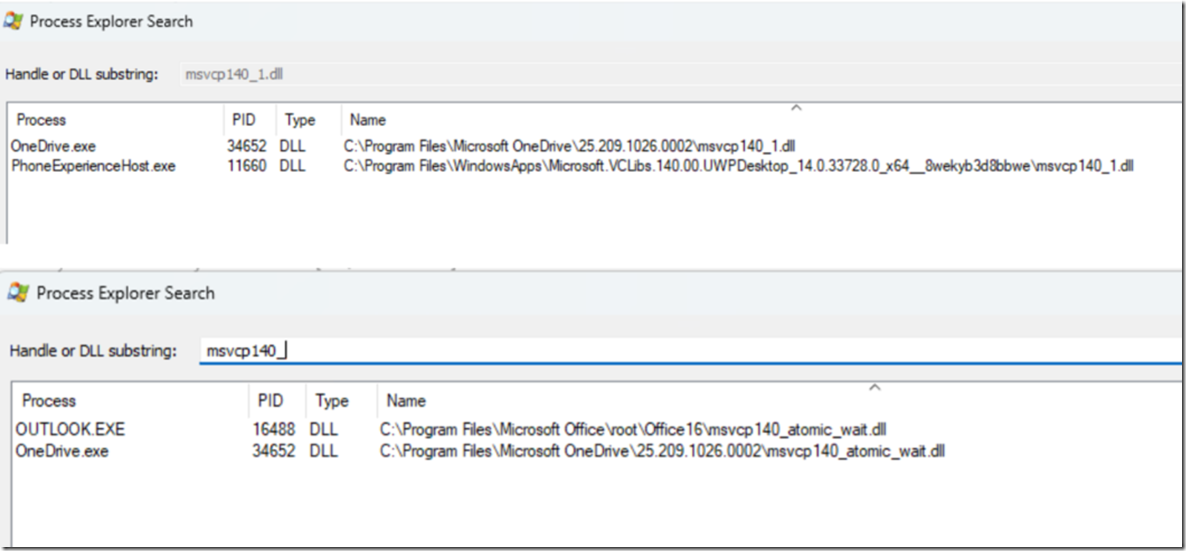
Process Explorer and FIND MSVCP140.DLL on a Server OS 2016 (Greetings to Gilles 😉
Here you can see a typical Dev machine and what uses Microsoft MSVCP140.DLL we checked if there is DLL hell
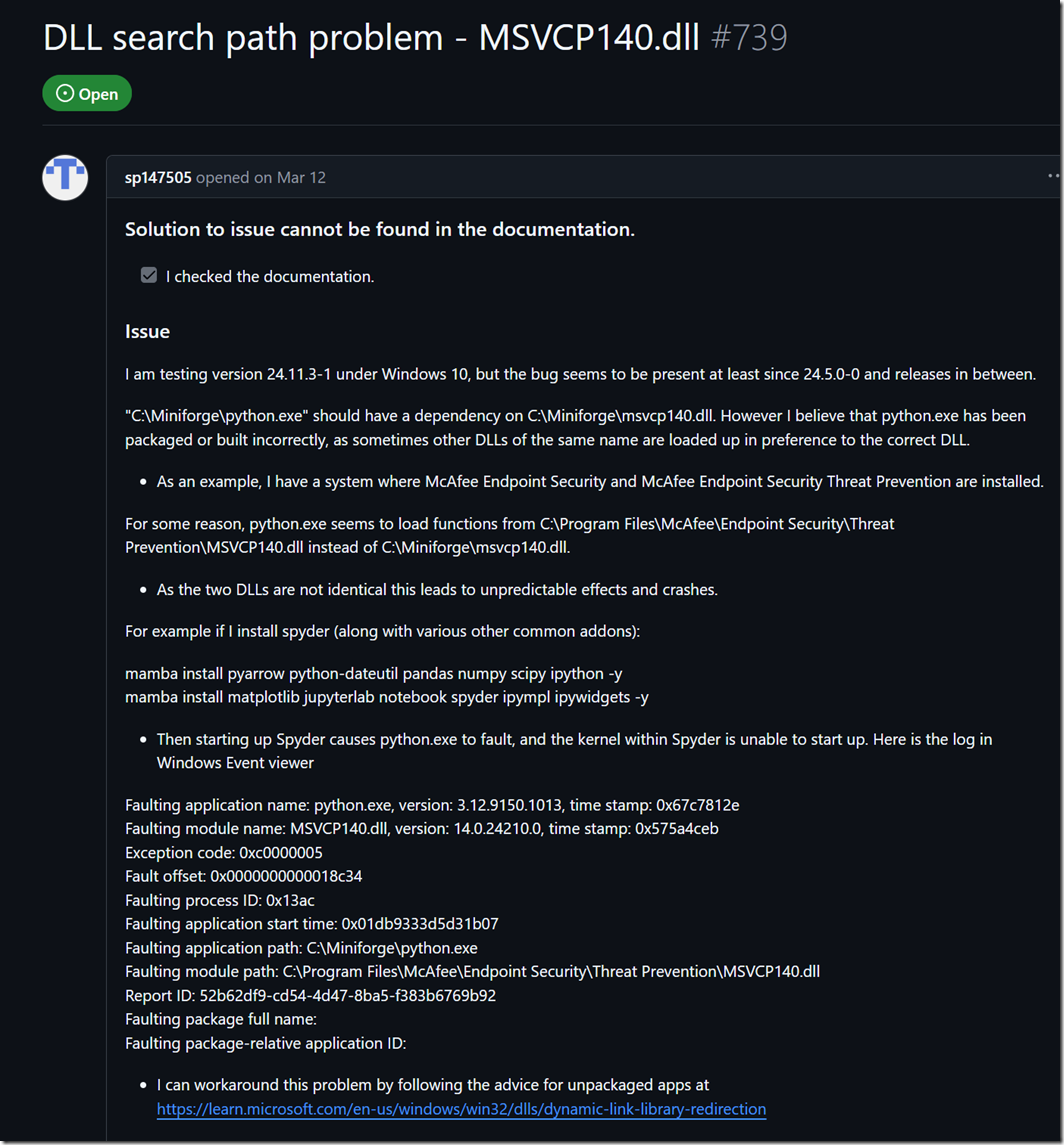
There was, and still is, an issue related to the Microsoft C++ runtime and Python releases. Four of our developers had different Python runtimes on their machines.
However, this only solved about 50% of the problems and we had machines with NO python who had the effect. The servers affected by the issue had no Python installed, so this is not a complete solution for all cases.
https://github.com/conda-forge/miniforge/issues/739
We has such machines and rate of affected machines was 50% of the ones which had some kind of Python on the machine. It was not sub component from VS 2022 it was installed local (You can see it from the TUX path like c:\python).The VS stuff is sure not there.
Affected Clients, solution on W11 where you are unable to uninstall Trellix ENS by HAND (ADD Software) or by EPO Client Uninstall Task
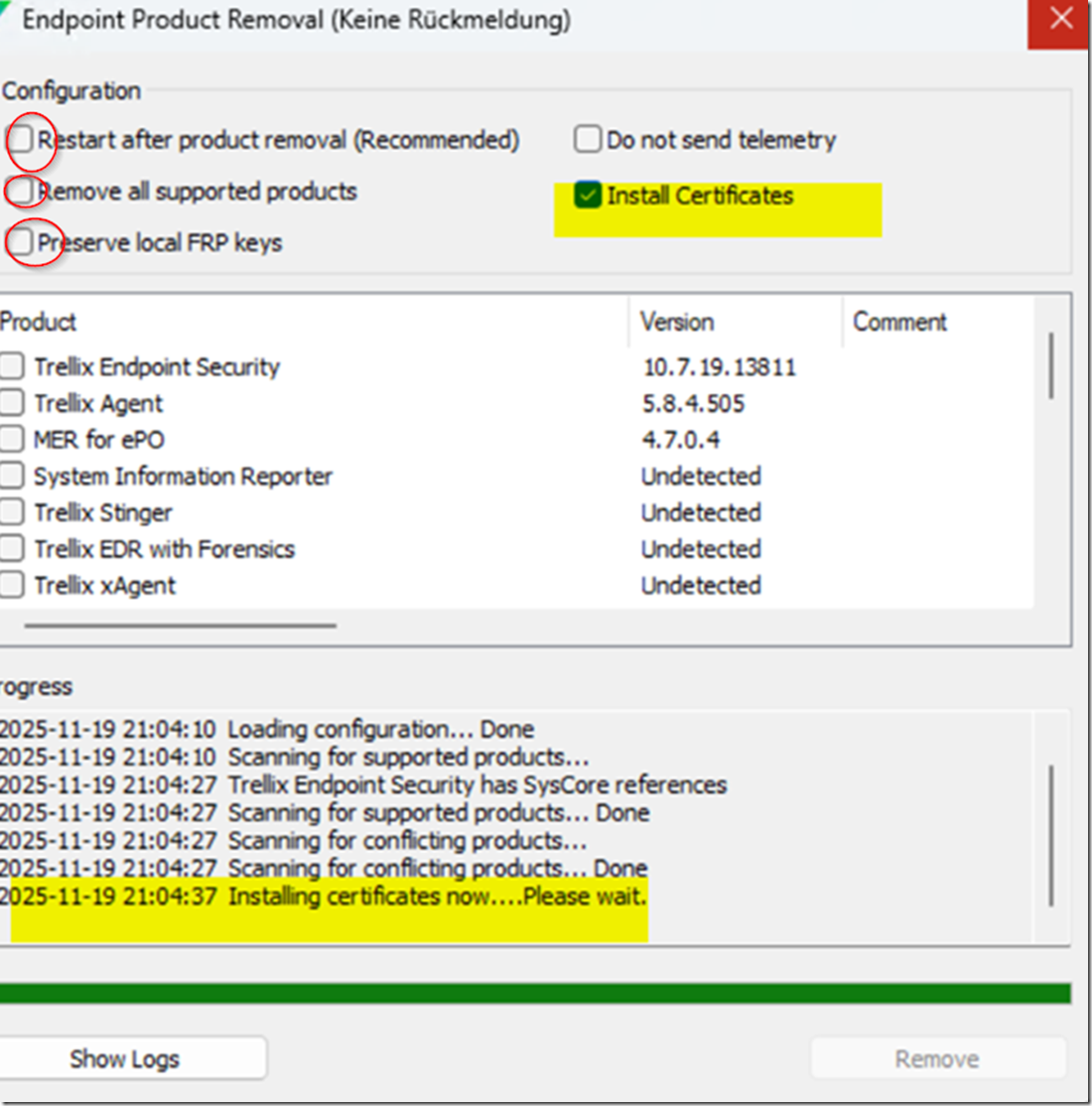
The only workaround for affected development machines was to completely uninstall all Trellix products using the Endpoint Product Removal tool (which can only be downloaded with a valid NAI license from the Trellix Portal).
We have never used this tool in a corporate environment and only on about 1 in 1,000 machines, typically once per year, when ENS could not be removed or migrated. These cases were mostly laptops or machines that had crashed during the ENS deployment or update process or battery down.This is the last resort and you are always unsure how stable the machine is afterwards if there are other security products running in parallel to Trellix.
We had all Certificates ajour this is just to show there is an option to do with that tool. Often missing Root Certs are the base of problems. But not in this case.
You can RUN this tool also from EPO to CLIENTS which works very well with the new version.
Affected Server 2016 + 2019 TS workaround | How to solve it
On the server OS, it works as described in the Trellix KB.
- Create a deployment job to uninstall modules in the following order: Firewall, Threat Protection, and lastly Platform.
- Create a deployment job to install the modules in the following order: Platform, Threat Protection, etc.
This solves the problem even without a reboot, as we are used to from Trellix.
Reminder: Before starting, make sure the server does not have a reboot flag set in ePO.
Example: Server 2016, Event 1000 crash.
Solution for larger customer:
a) Check your SIEM for Event 1000 from Trellix
b) This was not too reliable depending on what other people already tried to do. Like follow the Trellix KB and just try to uninstall and reinstall. Then the Event 1000 seemed to disappear so maybe search back more days/hours
c) We tried a PS which did not work very well and triggered most security things like SIEM so we mad a batch
d) we used TRELLIX EEDK to convert the batch to a TRELLIX package which you can then load into master repository of the EPO and deploy as task This worked very well (As I said best reliable Deployment ever)
@echo off
setlocal enabledelayedexpansion
:: ================================
:: McAfee/Trellix Registry + Event 1000 Checker
:: ================================
:: V1.0, 21.11.2025, www.butsch.ch, Mike Butsch
:: ================================
:: Checks for Event 1000 from Trellix and reads out the Trellix ENS Version
:: Change the logRoot var to your own server where you have a share called logfiles$ and adapted permission so the script can write things and create two directory
:: Make sure you \\server\logfiles$\00_TRELLIX
:: ================================
:: --- Part 0: Variables ---
set "computerName=%COMPUTERNAME%"
for /f "tokens=1-4 delims=:- " %%a in ("%date% %time%") do (
set currentDateTime=%%a-%%b-%%c %%d
)
:: set "logRoot=\\myeopserver\logfiles$\00_TRELLIX"
set "logRoot=\\myeopserver\logfiles$\00_TRELLIX"
set "problemFolder=%logRoot%\PROBLEM"
set "okFolder=%logRoot%\OK"
:: Create folders if missing
if not exist "%problemFolder%" mkdir "%problemFolder%"
if not exist "%okFolder%" mkdir "%okFolder%"
set "problemLog=%problemFolder%\%computerName%.txt"
set "okLog=%okFolder%\%computerName%.txt"
:: --- Part 1: Check Event ID 1000 (last 12 hours only) ---
set "pathToCheck=C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\mfeesp.exe"
set "eventExists=0"
:: 12 hours = 43,200,000 milliseconds
:: 07 days = 604,800,000 milliseconds
set "twelveHours=43200000"
for /f "tokens=*" %%E in ('wevtutil qe Application /q:"*[System[(EventID=1000) and TimeCreated[timediff(@SystemTime) <= 43200000]]]" /f:text') do (
echo %%E | findstr /i ^
/c:"C:\Program Files\McAfee\Endpoint Security\Endpoint Security Platform\MSVCP140.dll"
if not errorlevel 1 (
set "eventExists=1"
goto :FoundEvent
)
)
:FoundEvent
if "%eventExists%"=="1" (
set "outputLog=%problemLog%"
set "statusMessage=Event 1000 with the path exists! System is unstable please check."
) else (
set "outputLog=%okLog%"
set "statusMessage=No Event 1000 with the specified path found. Checked the last 12 hours of events"
)
:: --- Part 2: Write header ---
(
echo =========================================================================
echo McAfee/Trellix Registry + Event 1000 Checker
echo =========================================================================
echo V1.0, 21.11.2025, www.butsch.ch, Mike Butsch
echo =========================================================================
echo Checks for Event 1000 from Trellix and reads out the Trellix ENS Version
echo =========================================================================
echo DateTime: %currentDateTime%, ComputerName: %computerName%
echo Status: %statusMessage%
echo =========================================================================
echo.
) > "%outputLog%"
:: --- Part 3: Registry keys and values ---
set keys[0]=HKLM\SOFTWARE\McAfee\Endpoint\ATP
set keys[1]=HKLM\SOFTWARE\McAfee\Endpoint\AV
set keys[2]=HKLM\SOFTWARE\McAfee\Endpoint\Common
set keys[3]=HKLM\SOFTWARE\McAfee\AVSolution\AVS\AVS
for /l %%i in (0,1,3) do (
set "key=!keys[%%i]!"
echo Path: !key! >> "%outputLog%"
if "!key!"=="HKLM\SOFTWARE\McAfee\AVSolution\AVS\AVS" (
set values[0]=szAMCoreVersion
set valueCount=1
) else (
set values[0]=ProductVersion
set values[1]=BuildNumber
set values[2]=PatchVersion
set valueCount=3
)
for /l %%j in (0,1,!valueCount!-1) do (
set "val=!values[%%j]!"
if defined val (
set "found=N/A"
for /f "tokens=3*" %%a in ('reg query "!key!" /v "!val!" /reg:64 2^>nul') do (
if "%%b"=="" (
set "found=%%a"
) else (
set "found=%%a %%b"
)
)
echo !val! : !found! >> "%outputLog%"
)
)
echo. >> "%outputLog%"
)
echo ========================================================================= >> "%outputLog%"
echo Status: %statusMessage% >> "%outputLog%"
echo Done. Log written to %outputLog%
Solution: How to find client and server which have the Event 1000 when you have no SIEM in place or SIEM people don’t care because they only handle R7 😉
Use EEDK to deploy: Endpoint Deployment Kit
- download the EEDK tool from download licence portal
- Unpack ans start the EXE on the EPO server itself
- Change your logfile path in our script above save it as check_trellix.cmd
- Choose FILE from your location check_trellix.cmd
- Give it a name and version and under Command to RUN check_trellix.cmd
- Press “I accept the licnece termand and want to build a package”
- Go to your EPO server under MAIN REPOSITORY > Check in package >import the package
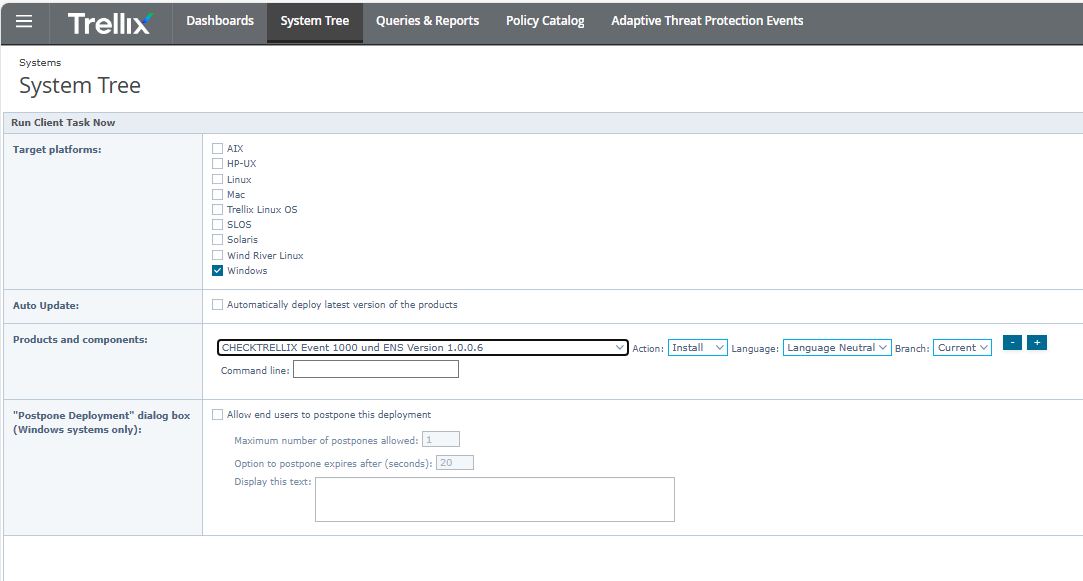
- Create a deployment task and choose the package
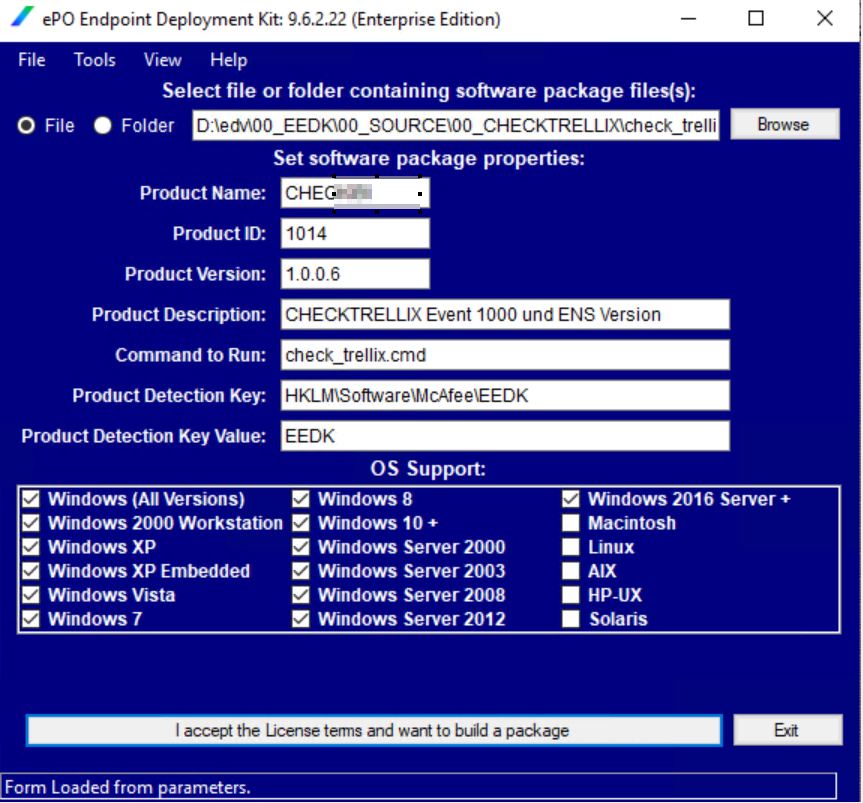
Deploy the self made EDDK package to your clients. This EEDK is absolute reliable and will Post back info into the share within a few seconds.
15.12.2025 Trellix released a new package that will TELL you pre-deploy of ENS 10.7.19 if you WOULD be affected
ENSW_DUP1075
Main part is:
reg query HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\AVSolution\InstallHistory\Versions /reg:64 | findstr “20.9.0 20.6.0 20.3.0 20.1.0 19.11.0 19.7.0 19.5.0 19.3.0 19.1.0 18.12.0 18.9.0 1.5.0”
Which checks if you have following Version in install history (any of those String would count and make it true)
- 20.9.0
- 20.6.0
- 20.3.0
- 20.1.0
- 19.11.0
- 19.7.0
- 19.5.0
- 19.3.0
- 19.1.0
- 18.12.0
- 18.9.0
- 1.5.0
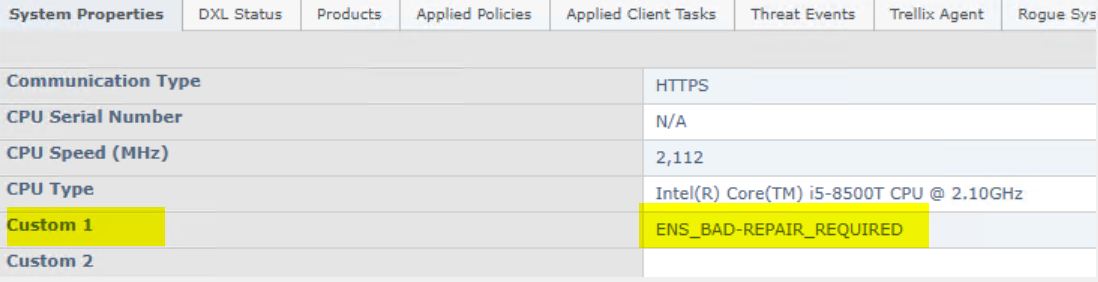
You can than see under the column “Custom 5” if you can UPDATE the server. As we understood if the field shows “WNSW_UPDATE5_BASE” wait with those machines because they MAY fail.
We have asked Trellix in case 17.12.2025 to explain us why and IF the migration path is relevant to WHICH version you installed INITITAL on the new servers WHEN etc.

Sample machine Server which showed as ENSW_UPDATE5_BASE
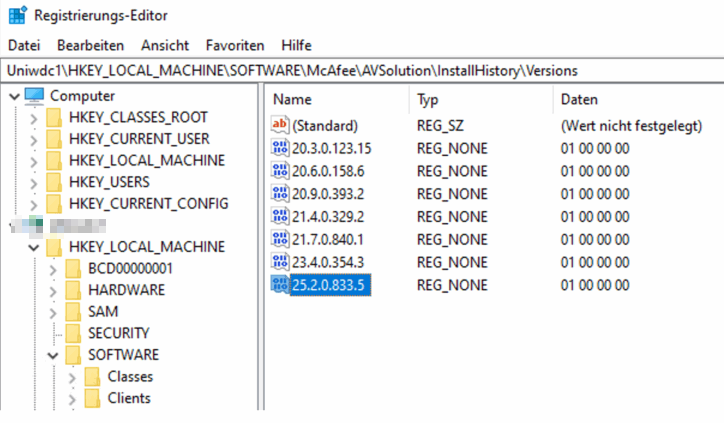
The server currently has this installed:
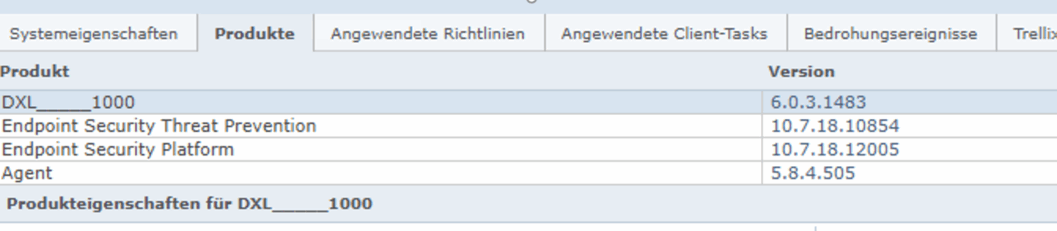
The Trellix script to check if YOU are affected BEFORE you try to migrate to 10.7.19
The main part is:
reg query HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\AVSolution\InstallHistory\Versions /reg:64 | findstr “20.9.0 20.6.0 20.3.0 20.1.0 19.11.0 19.7.0 19.5.0 19.3.0 19.1.0 18.12.0 18.9.0 1.5.0”
If that is TRUE (Finds something) then the client/server would eb affected from the update problem.
:: TA Custom Property 5 value "ENSW_UPDATE5_BASE" indicates that the Systems originated from ENS UPDATE 5 baseline version susceptible to VC runtime issues.
setlocal ENABLEEXTENSIONS
setlocal EnableDelayedExpansion
:: Set environment to current product folder
pushd "%~dp0"
:: Initialize agent_path variable
set agent_path=
:: ---------------------------
:: Find path to McAfee Agent first
::Read information from 64 bit
set KEY_NAME0=HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Network Associates\ePolicy Orchestrator\Agent
set VALUE_NAME0=Installed Path
FOR /F "skip=2 tokens=1,3*" %%A IN ('REG QUERY "%KEY_NAME0%" /v "%VALUE_NAME0%" /reg:64 2^>nul') DO (set "agent_path=%%C")
if "%agent_path%" == "" GOTO Read_32_bit_information
set agent_path=%agent_path%\..\
GOTO Set_Custom_Values
:Read_32_bit_information
set KEY_NAME0=HKEY_LOCAL_MACHINE\SOFTWARE\Network Associates\ePolicy Orchestrator\Agent
set VALUE_NAME0=Installed Path
FOR /F "skip=2 tokens=1,3*" %%A IN ('REG QUERY "%KEY_NAME0%" /v "%VALUE_NAME0%" 2^>nul') DO (set "agent_path=%%C")
if "%agent_path%" == "" GOTO Script_Failed
:: ---------------------------
:Set_Custom_Values
:: check for ENS Update 5 base version , Write results to Custom Props
:: Get software package source directory and set as variable SRCDIR
SET SRCDIR=
for /f "delims=" %%a in ('cd') do @set SRCDIR=%%a
:: Check for ENS Update 5 base version
reg query HKEY_LOCAL_MACHINE\SOFTWARE\McAfee\AVSolution\InstallHistory\Versions /reg:64 | findstr "20.9.0 20.6.0 20.3.0 20.1.0 19.11.0 19.7.0 19.5.0 19.3.0 19.1.0 18.12.0 18.9.0 1.5.0"
if %errorlevel% EQU 1 GOTO end_of_upd5_check
%comspec% /c ""%agent_path%\maconfig.exe" -custom -prop5 "ENSW_UPDATE5_BASE""
:end_of_upd5_check
%comspec% /c "%agent_path%\cmdagent.exe" -p
GOTO end_of_file
:Script_Failed
echo "No reg value found - Script failed."
ENDLOCAL
Exit /B 1
:end_of_file
:: Exit and pass proper exit to agent
ENDLOCAL
Exit /B 0
Original post from Trellix which is very thin related to massive problem it has caused for some customers
Status 20.11.2025, ongoing problem, Trellix has NOT given a full working solution for all problems
https://thrive.trellix.com/s/article/000014988?language=en_US
Known Issue: Trellix Endpoint Security is not functional after upgrading to version 10.7.19 |
EnvironmentTrellix Endpoint Security (ENS) SymptomThe ENS service ceases operation or experiences an unexpected termination following an upgrade to version 10.7.19 from an earlier release. The Windows Event log shows the following:
CauseThe product deployment was incomplete as it failed to replace all necessary binaries due to an incompatibility with the Microsoft runtime environment. WorkaroundFollow these steps to resolve the issue:
|


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.