Microsoft has added some new options in the Server 2008R2 GPO’s for Windows 7 to handle Intranet or Proxy bypass Sites automatic as Local Intranet. But still there is lot of work and trouble. You may have to fix Attachment User Policy for .EXE/.CHM Files and also as usual the Intranet Zone Files.
You can manually check on the Windows 7 client if you have no permission as user. Most of the times the VIEW of the ZONING is forbidden for regular Domain user and you can’t scroll down. Just verify in the Registry as user if YOU can start regedit or other reg dump tools.
HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMapKey
Regedit client view of the Zone Mapping:
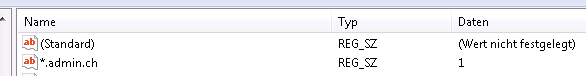
Regedit server view of the Zone Mapping:

The 1 on the right means LOCAL INTRANET
GPO / Mostly we put this into a W7_Internet_Explorer_IE9_U GPO
USER PART > Windows Components/Internet Explorer/Internet Control Panel/Security Pages
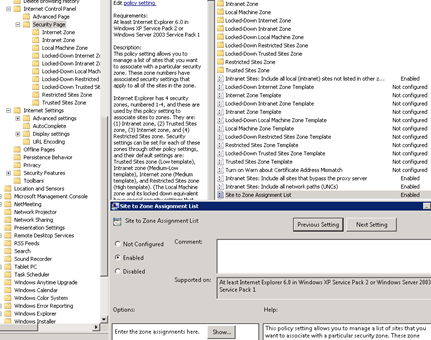
Patterns/Parameter you can use:
Examples of valid patterns that can be used are:
*://*.microsoft.com
http://*.microsoft.ch
ftp://137.54.23.41/
file:\\localsvr\myshare
*://137.54.100-200.*
Examples of invalid patterns:
ftp://*
If applicable please check User Configuration — >> Administrative Templates — >> Internet
Explorer — > Internet Control Panel — >> Security Page–>>Site
to Zone Assignment list>>Click on Show. Remove invalid entries.
There is very limited info on MSDN about the exact definition you may use:
http://technet.microsoft.com/en-us/library/cc736412.aspx
If you are handling trouble with opening .EXE Files or links from Intranet Servers these options are also important BUT risky!
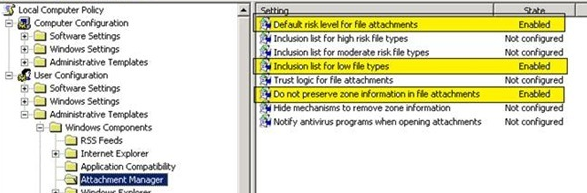
Configuration Settings:
- Default risk level for file attachments: Set it to Enabled and Set the default risk level to[Low Risk]
- Inclusion list for low file types: Set it to Enabled and add the file extension [.exe;.vbs;.msi]
- Do not preserve zone information in file attachments: Set it to Enabled.
Screenshot of the policy:


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.