The WSUS Server Console on a 2012R2 server suddenly does not work anymore. You checked %appdata%\Roaming\Microsoft\MMC\WSUS (Backup, Remove try if it works and restore if did not solve) and this did not help.
You checked all Services and did a reboot of the WSUS and checked space and Size of Internal DB.
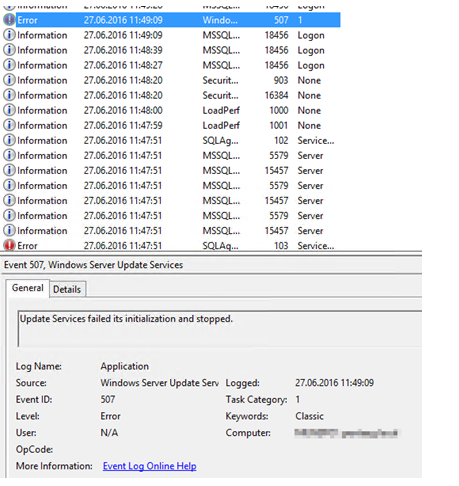
Error: Event 507, Windows Server Update Server
Error: Event 7031, The WSUS Server Service terminated


|
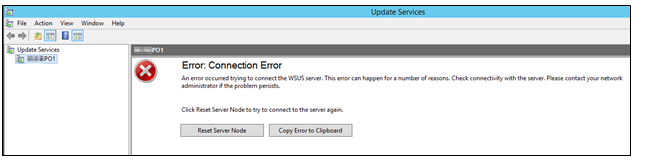
Error as Text from GUI |
|
The WSUS administration console was unable to connect to the WSUS Server via the remote API. Verify that the Update Services service, IIS and SQL are running on the server. If the problem persists, try restarting IIS, SQL, and the Update Services Service. The WSUS administration console has encountered an unexpected error. This may be a transient error; try restarting the administration console. If this error persists, Try removing the persisted preferences for the console by deleting the wsus file under %appdata%\Microsoft\MMC\.
System.IO.IOException — The handshake failed due to an unexpected packet format. Source System Stack Trace: at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest) at System.Net.Security.SslState.StartReceiveBlob(Byte[] buffer, AsyncProtocolRequest asyncRequest) at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest) at System.Net.Security.SslState.ForceAuthentication(Boolean receiveFirst, Byte[] buffer, AsyncProtocolRequest asyncRequest) at System.Net.Security.SslState.ProcessAuthentication(LazyAsyncResult lazyResult) at System.Threading.ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx) at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx) at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state) at System.Net.TlsStream.ProcessAuthentication(LazyAsyncResult result) at System.Net.TlsStream.Write(Byte[] buffer, Int32 offset, Int32 size) at System.Net.ConnectStream.WriteHeaders(Boolean async) ** this exception was nested inside of the following exception **
System.Net.WebException — The underlying connection was closed: An unexpected error occurred on a send.
Source Microsoft.UpdateServices.Administration
Stack Trace: at Microsoft.UpdateServices.Administration.AdminProxy.CreateUpdateServer(Object[] args) at Microsoft.UpdateServices.UI.AdminApiAccess.AdminApiTools.GetUpdateServer(String serverName, Boolean useSecureConnection, Int32 portNumber) at Microsoft.UpdateServices.UI.SnapIn.Scope.ServerSummaryScopeNode.ConnectToServer() at Microsoft.UpdateServices.UI.SnapIn.Scope.ServerSummaryScopeNode.get_ServerTools() |




Solution:
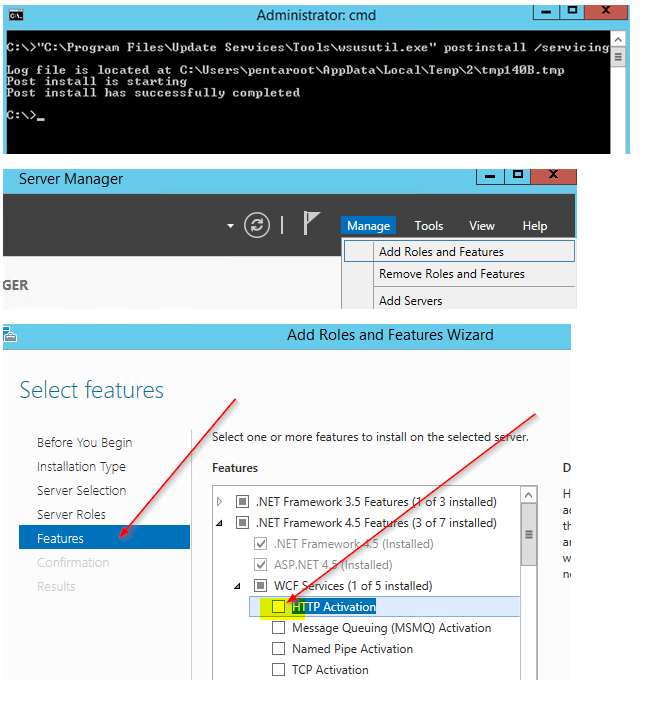
“C:\Program Files\Update Services\Tools\wsusutil.exe” postinstall /servicing


-
Console should work again
This article describes an update to a feature that enables Windows Server Update Services (WSUS) to natively decrypt Electronic Software Distribution (ESD) in Windows Server 2012 and Windows Server 2012 R2. Before you install this update, see the Prerequisites section.
Note You must install this update on any WSUS server that is intended to sync and distribute Windows 10 upgrades (and feature updates) that are released after May 1, 2016.
How to get this update
Important If you install a language pack after you install this update, you must reinstall this update. Therefore, we recommend that you install any language packs that you need before you install this update. For more information, see Add language packs to Windows.
Windows Update
This update is available on Windows Update. For more information about how to run Windows Update, see How to get an update through Windows Update.
Update detail information
Prerequisites
To apply this update in Windows Server 2012 R2, you must have April 2014 update rollup for Windows RT 8.1, Windows 8.1, and Windows Server 2012 R2 (2919355) installed.
Registry information
To apply this update, you don’t have to make any changes to the registry.
Restart requirement
You may have to restart the computer after you apply this update.
Update replacement information
This update can be installed on top or in place of KB3148812.
More information
Manual steps required to complete the installation of this update
-
Open an elevated Command Prompt window, and then run the following command (case sensitive, assume “C” as the system volume):
“C:\Program Files\Update Services\Tools\wsusutil.exe” postinstall /servicing
-
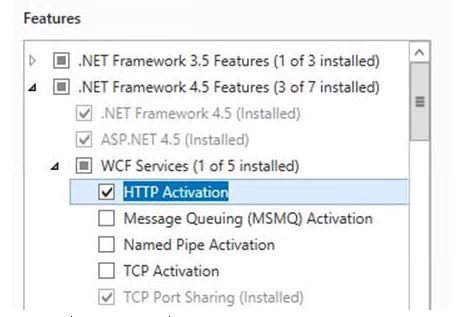
Select HTTP Activation under .NET Framework 4.5 Features in the Server Manager Add Roles and Features wizard.


-
Restart the WSUS service.
If SSL is enabled on the WSUS server
-
Assign ownership of the Web.Config file to the administrators group (run at an elevated command prompt):
-
takeown /f web.config /a
-
icacls “C:\Program Files\Update Services\WebServices\ClientWebService\Web.config” /grant administrators:f
-
Locate the Web.Config file in the following path:
C:\Program Files\Update Services\WebServices\ClientWebService\Web.Config
-
Make the following changes in the file.
Note This code sample represents a single text block. The line spacing is used only to emphasize the text changes, which are shown in bold.
-
<services>
-
<service
-
name=”Microsoft.UpdateServices.Internal.Client”
behaviorConfiguration=”ClientWebServiceBehaviour”>
<!–
These 4 endpoint bindings are required for supporting both http and https
–>
<endpoint address=””
binding=”basicHttpBinding”
bindingConfiguration=”SSL”
contract=”Microsoft.UpdateServices.Internal.IClientWebService” />
<endpoint address=”secured”
binding=”basicHttpBinding”
bindingConfiguration=”SSL”
contract=”Microsoft.UpdateServices.Internal.IClientWebService” />
<endpoint address=””
binding=”basicHttpBinding”
bindingConfiguration=”ClientWebServiceBinding”
contract=”Microsoft.UpdateServices.Internal.IClientWebService” />
<endpoint address=”secured”
binding=”basicHttpBinding”
bindingConfiguration=”ClientWebServiceBinding”
contract=”Microsoft.UpdateServices.Internal.IClientWebService” />
</service>
</services>
-
Add the multipleSiteBindingsEnabled=”true” attribute to the bottom of the Web.Config file, as shown:
-
</bindings>
-
<serviceHostingEnvironment aspNetCompatibilityEnabled=”true” multipleSiteBindingsEnabled=”true” />
</system.serviceModel


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.