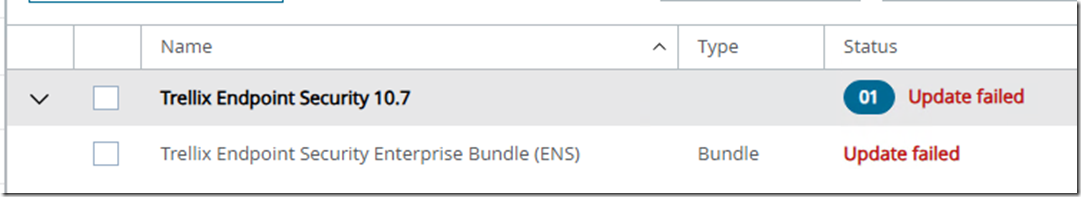
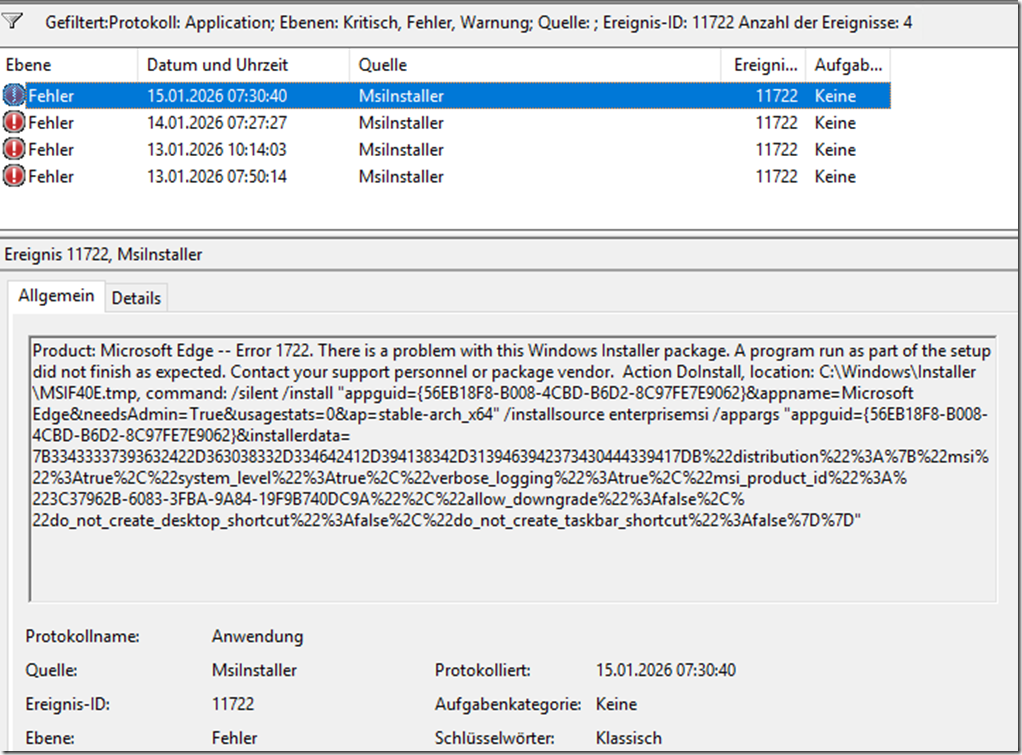
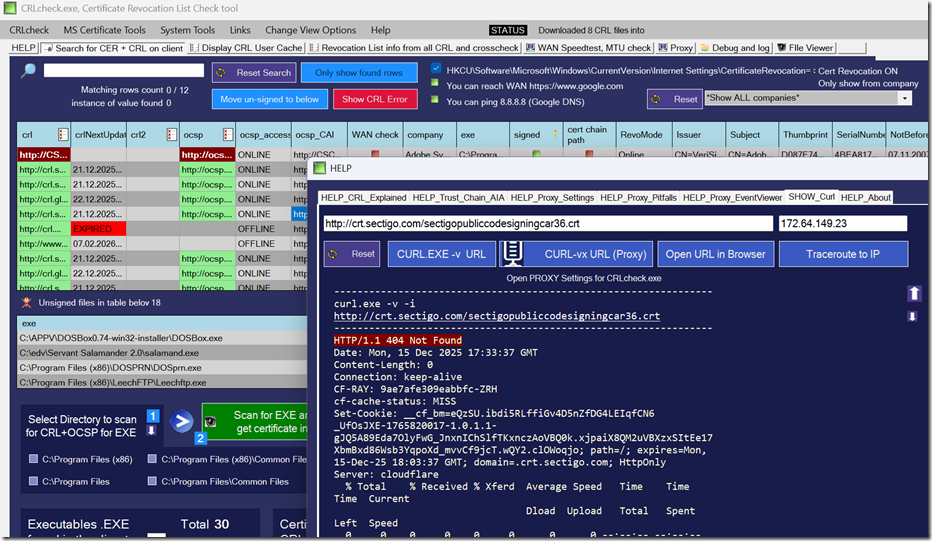
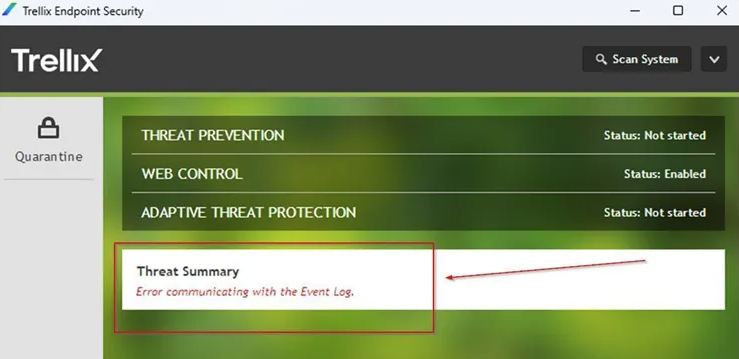
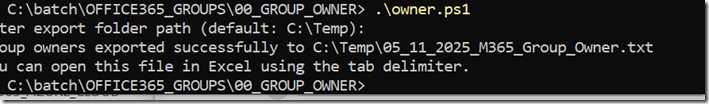
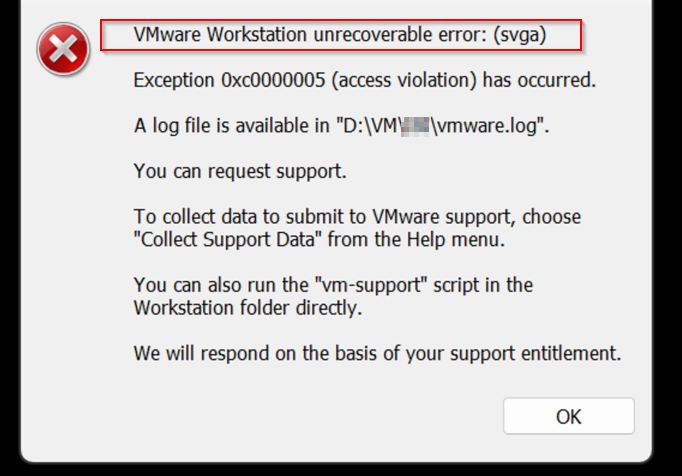
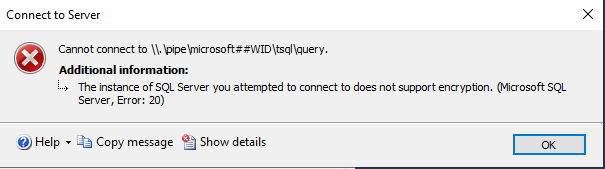
Trellix ENS 10.7.20 bundle Update failed, Extension ENDP_GS_1000, version 10.7.20.15122 is not compatible with this version of epolicy Orchestrar
Tasks/What you try to do: You try to integrate or update the new Trellix ENS 10.7.20 from last week into ePO to try the new ransomware options and also test if we can finally exclude On-Access rules by MD5 added to filenames. The update of the bundle via Software Manager fails. The DLL replacement […]