We just did finish our first look at the new MVSION Client when already a new Release came out the last days. https://kc.mcafee.com/corporate/index?page=content&id=SNS1746
This report reflects version 18.10.2.2.

Main reason business drivers for the MVSION version for us are:
-
AMSI integration and usage of Windows Defender as base pattern scanner (You can only scan malware where it runs in un-encrypted form > Thus only MS can do…) So powershell malware is captured by MS Windows Defender. Why not do it for the rest of the pattern stuff?
-
A slimmer Platform for VDI solution where the FULL ENS Suite 10.6.X would be too heavy. We still think the full ENS 10.6.1 with ATP Module as 3rd module brings the best security together with TIE and ATD-Sandbox. We did take a look at MOVE but from a long term view this would throw the customer back 5 years from what he has NOW on FAT clients with the working suites. We are very happy with what the FULL ENS 10.6.1 does for all our customers from small to Enterprise. They key changer is just the packet storm, re-setup of VDI Clients.
Main reason we think Mcafee pushes MVSION:
- Push the MVision Mobile Version > New company the bought > Zimperium
- Push their SAAS Cloud
For the Cloud?
Here are some impressions from MVSION ONPREMISE. You don’t want to manage EPO in Cloud when a brute force DOOS rips you LAN and WAN interface apart right? You also don’t want an OUTBREAK when McAfee schedules their CLOUD downtime and reports to all malwares coder via SNS Alerts.
The 18.10.2.2 Package and Extension (EPO on premise)
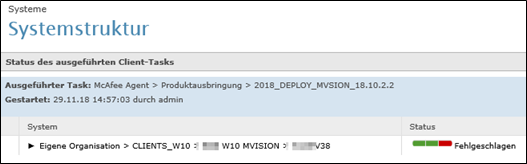
Deployment of MVSION client fails if ENS 10.X on machine.
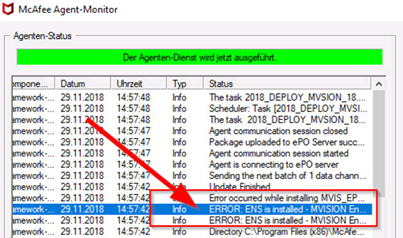
You can see the error in the Event
Run a JOB to Uninstall ENS from BOTTOM 2 TOP (Reverse order you install it)
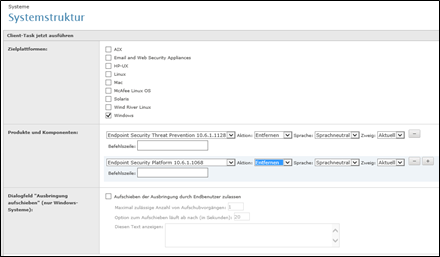
After a reboot, you can deployment MVSION client.
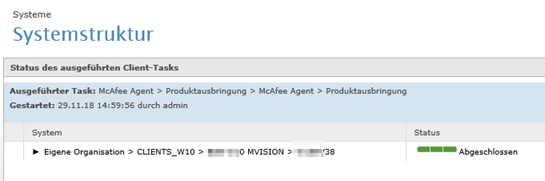
The Client show up on Windows 10
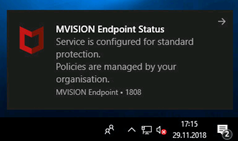
Here is the information you see in Agent:
Some Directory structure
Logfiles
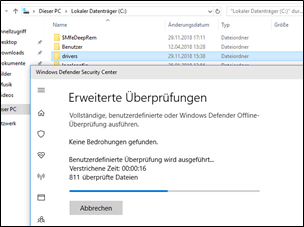
Windows Defender appears as it did before you do not notice anything there.
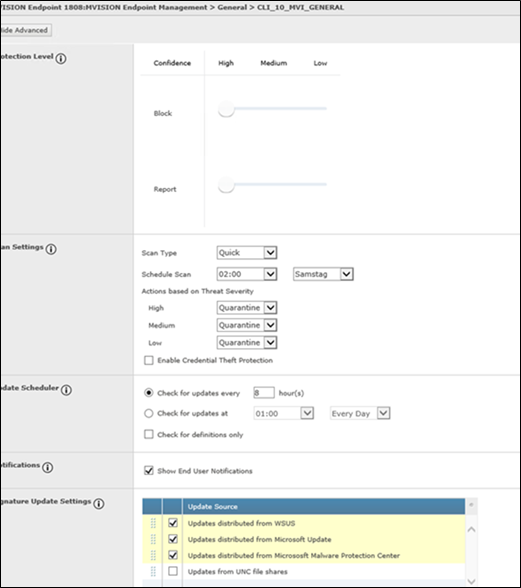
Policies
First Exclusion GENERAL
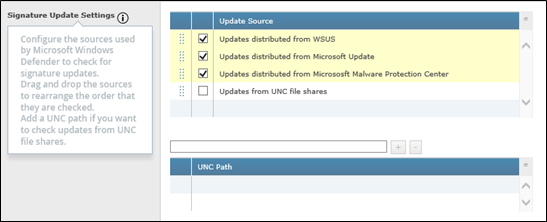
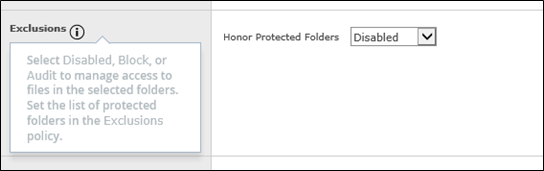
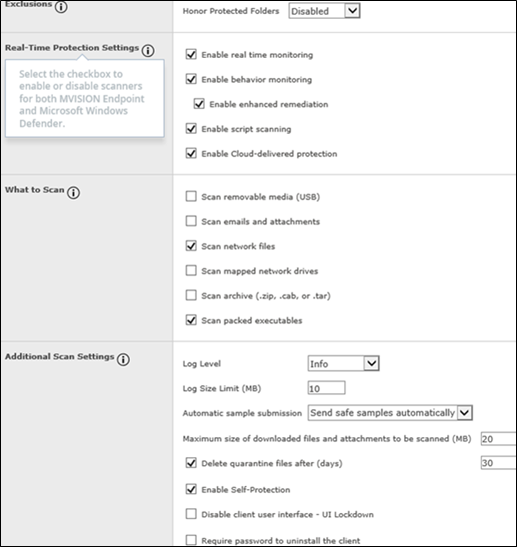
Second Policy: EXCLUSIONS
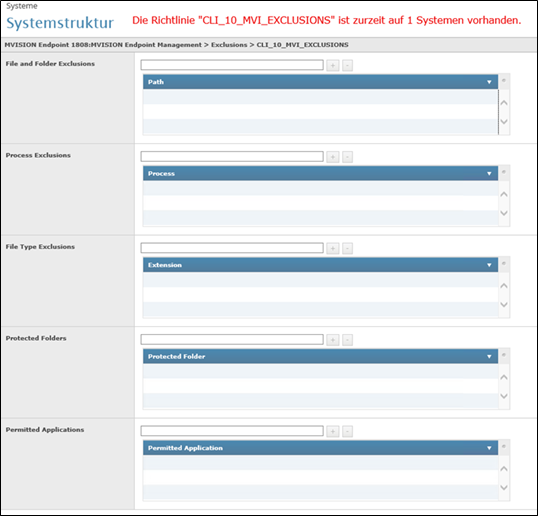
Here what we clearly miss today is:
*The granular drilldown to exclude process on single functions
* The exclude with MD5. You don’t want really FILESNAMES like 10 years ago?
We understand that Mcafee runs the simpler and were too complex line but this goes too far. We see the first problem here in the DUAL Management (1 Windows Defender and 2 Mcafee Module).
The Windows Defender does not allow Hash Exclusion and they wanted a central exclusion. We were so happy they finally included the ONE POINT Exclusion for VSE 8.8 Patch 12 bur here we miss something in the opposite way.
On existing EPO 5.9.1 you see following after integration of the MVSION POLICY
EPO GUI which has the same feel and look as under EPO 5.10 (New style….) Look like the new security vendor styles with lots of colors for managers.
Here they have colors on the TIE Server we had to beg for years so we see with GREEN OR RED of a file would run.
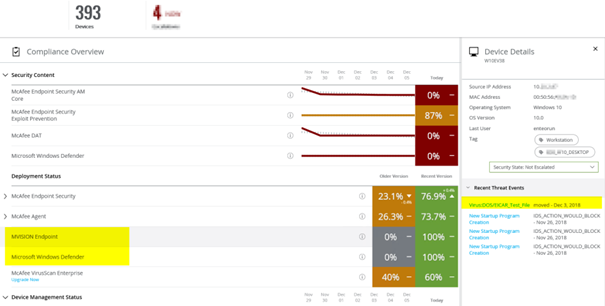
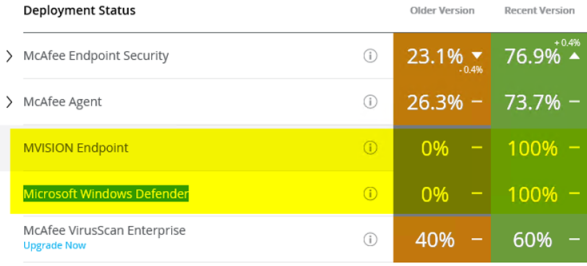
If you Like graphs in EPO 5.10 style? Well we have 73.7% because older server OS has to run older Mcafee Agents. On the other hand even a newbie sees now that there is VSE 8.8 Patch12 out OR 40% of the server has not been migrated (Maybe complex Exchange DAG cluster in isolated VLAN etc. or OLD Server OS) That was kind of never useful we think.
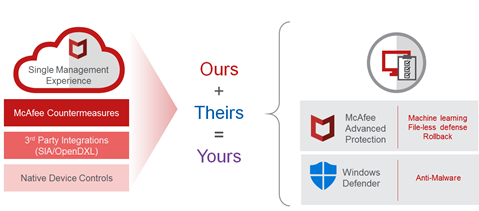
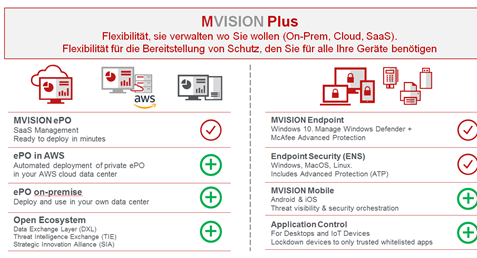
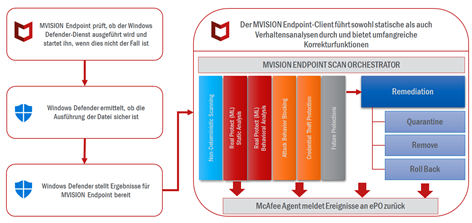


 Click on the Category button to get more articles regarding that product.
Click on the Category button to get more articles regarding that product.